































As we saw in my last blog, the network plays a key role in defending critical infrastructure and IoT. The devices that we are connecting drive our business, enabling us to make smarter decisions and gain greater efficiency through digitization. But how do we ensure those connected devices are acting as intended? From an industrial operations perspective, we need to know that plant operations are nominal, irrespective of cyber threat. The network is well positioned to assist us in detecting misbehaving devices.
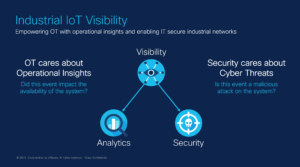
In order to have assurance of business operations, it is critical to have visibility and awareness into what is occurring on the network at any given time. Network telemetry offers extensive and useful detection capabilities which can be coupled with dedicated analysis systems to collect, trend and correlate observed activity. In the security world we can infer much from network telemetry, from malware behaviour and reconnaissance, to data exfiltration. It is even possible to infer to some extent what is contained in encrypted traffic. Not only can we use this traffic for detection, but also for investigation. Having a historical record of communication also assists with investigating incidents. We can see, for example, what other hosts may have talked to a command and control server, or we can look at any lateral movement from a host.
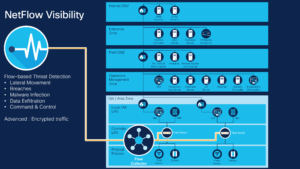
The first step is to collect Netflow, which is a unidirectional sequence of packets with some common properties that pass through a network device. These collected flows are exported to an external device, the NetFlow collector. Network flows are highly granular; for example, flow records include details such as IP addresses, packet and byte counts, timestamps, Type of Service (ToS), application ports, input and output interfaces.
Exported NetFlow data is used for a variety of purposes, including enterprise accounting and departmental chargebacks, ISP billing, data warehousing, network monitoring, capacity planning, application monitoring and profiling, user monitoring and profiling, security analysis, and data mining for marketing purposes.
For most network devices (including many ruggedized devices used in OT environments), Netflow is simply an option you can turn on sending this data to a Netflow collector. Lower-end switches may not have this option; however, a span port can send traffic to a Netflow Sensor to accomplish this task. Gathering network telemetry visibility is the first step for organisations. The next steps are to utilise tools that can analyse the traffic and look for behavioural anomalies. For more advanced use cases, Encrypted Traffic Analytics (ETA) offers insights into encrypted traffic as well.
The problem of scale in IoT, is also evidenced in security incident detection and response, where we have more traffic to review, and accordingly, more events. We need tools to help us, and Machine Learning (ML) and Artificial Intelligence (AI) based tooling are important technologies, particularly when it comes to network behaviour. Devices, as opposed to humans, tend to have very defined behaviour, so leveraging ML and AI to observe and baseline this behaviour offers high fidelity alert sources.
Machine Learning in Network Security
To really accelerate detection and lower our median time to detect, we need all our tools to work together. In the previous post we discussed network context and understanding what a device policy should be, at scale. What if we could leverage that same information to assist with detection? Understanding contextual information and what a device's policy should be, can help increase fidelity of behavioural alerts. Investigators also benefit from having this information integrated into their tools, which helps speed investigations.
November is Critical Infrastructure Security and Resiliency Month, so head over to our Trust Center to learn more about critical infrastructure protection and comprehensive visibility and network traffic security analytics.
 Hot Tags :
Cybersecurity
Internet of Things (IoT)
Featured
Artificial Intelligence (AI)
Cisco Stealthwatch
Machine Learning (ML)
Network Telemetry
network visibility
Critical Infrastructure Protection
Hot Tags :
Cybersecurity
Internet of Things (IoT)
Featured
Artificial Intelligence (AI)
Cisco Stealthwatch
Machine Learning (ML)
Network Telemetry
network visibility
Critical Infrastructure Protection