































It's an exciting time for organizationsthat are migrating to Industry 4.0. Over the last few decades, industrial control systems (ICS)haveenabled modern industrialautomation.Today,Industrial Internet of Things (IIoT) technologies present new opportunities toincrease operational efficiency and launch a new generation of industrial products and services.
But first, organizationsmust address security.Last week at Cisco Live in Barcelona we announced the first release of Cisco Cyber Vision, a solution designedtoaddress these security challenges so thatorganizations cancontrol cybersecurity risks andcapture the benefits ofIndustry 4.0.
Protecting industrial operations is a very specific challenge that can't be addressed with traditional IT security tools. Industrial processes can't come to a halt toinstalla patch. Disruption can have a devastating impact on human lives and/or the environment. To further complicate matters, attacks can be difficult to detect because they are often custom made and look like legitimateprocessinstructions.
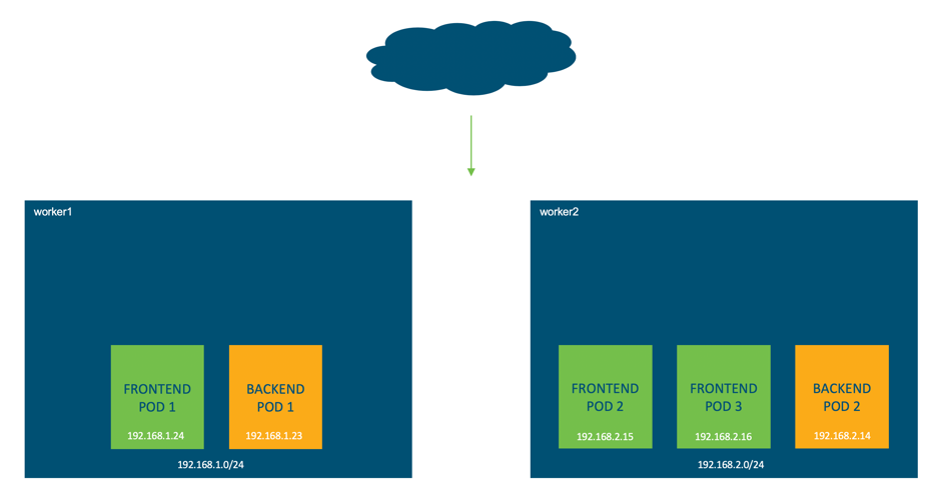
Cisco Cyber Vision isspecificallydesigned for industrial organizationsto ensure continuity, resilience,and safety of their operations. It provides full visibility into theICS Before we get into pod-to-pod communication, we should first look at how the addresses and interfaces of our environment have been configured. *** IMPORTANT POINT: *** Every Kubernetes pod receives its own unique IP address. As we previously saw, you can have multiple containers per pod. This means that all containers in a pod share the same network namespace, IP address and interfaces. Kubernetes and containers rely heavily on Linux namespaces to separate resources (processes, networking, mounts, users etc) on a machine. "Namespaces are a feature of the Linux kernel that partitions kernel resources such that one set of processes sees one set of resources while another set of processes sees a different set of resources." "Network namespaces virtualize the network stack. Each network interface (physical or virtual) is present in exactly 1 namespace and can be moved between namespaces. Each namespace will have a private set of IP addresses, its own routing table, socket listing, conn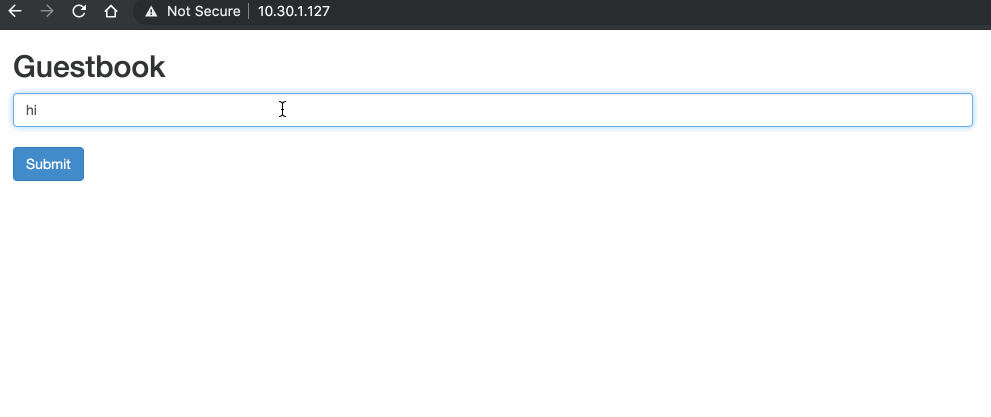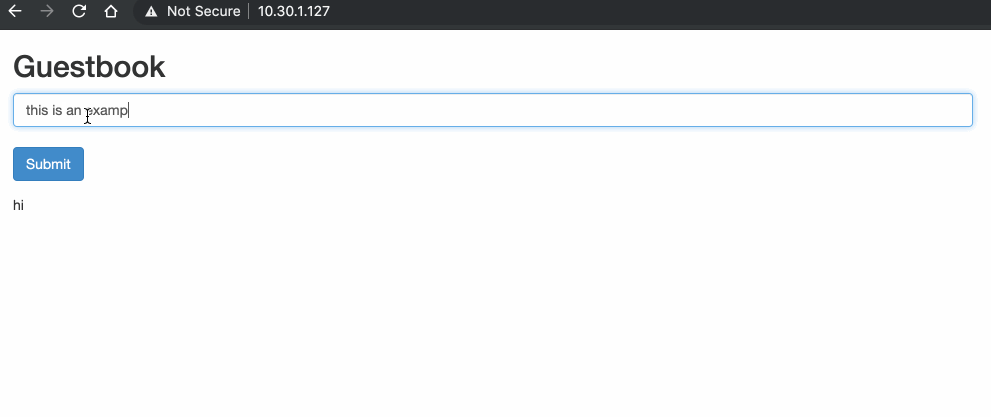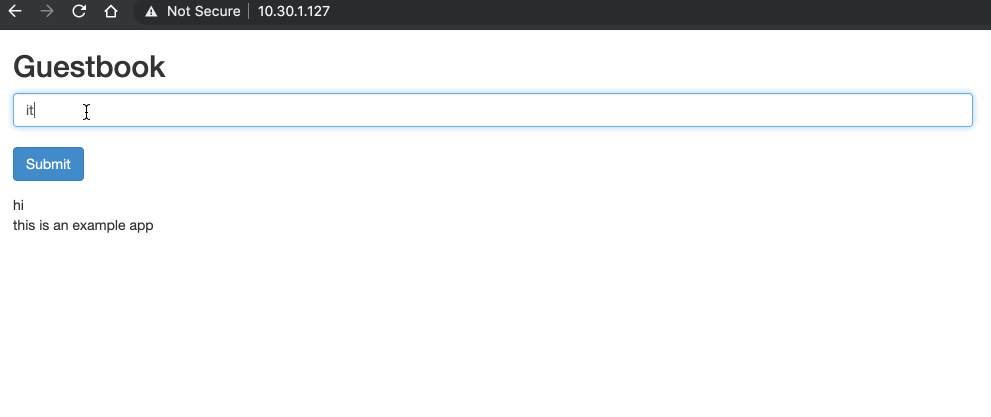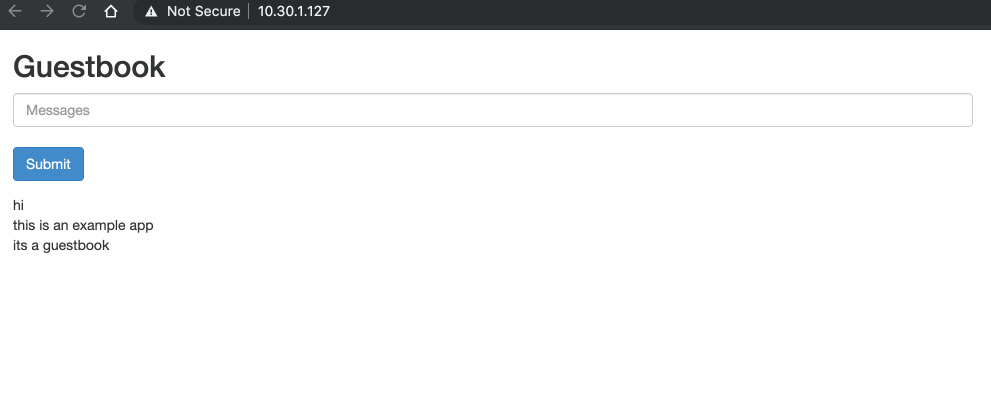
Network Namespaces
 Hot Tags :
Cybersecurity
Internet of Things (IoT)
Networking
#Security
Cisco Industrial IoT (IIoT)
IT
Cisco Secure Industrial Networking
Industry 4.0
OT
Hot Tags :
Cybersecurity
Internet of Things (IoT)
Networking
#Security
Cisco Industrial IoT (IIoT)
IT
Cisco Secure Industrial Networking
Industry 4.0
OT