































 This post is coauthored by Andrew Tsonchev.
This post is coauthored by Andrew Tsonchev.
Anyone can purchase an exploit pack (EP) license or rent time on an existing EP server. The challenge for threat actors is to redirect unsuspecting web browsing victims by force to the exploit landing page with sustained frequency. Naturally, like most criminal services in the underground, the dark art of traffic generation is a niche specialty that must be purchased to ensure drive-by campaign success. For the past year we have been tracking a threat actor (group) that compromises legitimate websites and redirects victims to EP landing pages. Over the past three months we observed the same actor using malvertising -leveraging content delivery networks (CDNs) to facilitate increased victim redirection -as part of larger exploit pack campaigns.
 Increasing victim web redirection as part of larger exploit pack campaigns
Increasing victim web redirection as part of larger exploit pack campaignsThreat intelligence and incident response rely on triggers and anomalies to initiate deeper investigations. Two weeks ago, TRAC detected victim web redirection to a Styx exploit pack which uses common landing page JavaScript. We further confirmed that the malicious redirection activity was part of a larger ongoing campaign.
On April 1st, 2014 we began blocking specific malicious web requests from 256 users in 186 companies. The requests were destined for the following thirteen domains (which we label "stage two domains"), all of which resolved to 77.245.75.237 (Redstation Limited -Dedicated Server Hosting, Great Britain). The following stage two domains represent the final phase of the attack, but it was only the beginning of a lengthy historical incident response trail.
ovcn.drinkstablesflowws.us
gebm.medicksflowertype.net
hcg.onimevideosfloss.us
hnrf.drinkstablesflowws.us
mc.googledrinkcs.net
nckjf.medicksflowertype.net
nyjsz.drinkstablesflowws.us
prkun.googledrinkcs.net
qluht.medicksflowertype.net
tcyu.drinkstablesflowws.us
uhofz.medicksflowertype.net
vohx.googledrinkcs.net
xyl.medicksflowertype.net
Example of a full EP landing page URI for each of the above (stage two) domains:
/0BD3-Gr0D5-4417_g1I0-Vhk30vc_li0t-3G30bn6-M0B4Un-0URJ_j0ByWy0b_THP/08L/HG0KFU/J164A00PKj/m0Cf_ol0VWk_p13ER702f-Lv0f1j-j08_lYt04-WHQ0_FZrL/0KEf-70e/xy5/0gDYM0Gsn_h0BmFr_0WY1_50X2U/F05/f0W_0bKXG034_Sz130fC0_5mB_808n8-J0ol/ov0JpF_Y0e1g20/w5st1-4nxu/12MUS0RP/zc0Rr-O817d/VC/0GMkB0m_AeZ_0lq-T50y_AzI0Em-0F-0sccB-0buQ/Q0mJiy/0bie/v0eiLr-0lk_jI02/rHX/
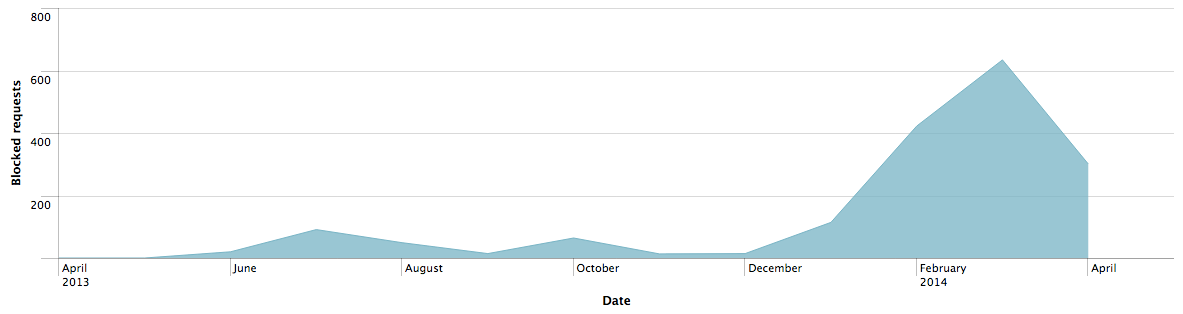
We subsequently extracted the referrers ("stage one domains") that had driven our customers to the blocked exploit pack domains. The chart below depicts the stage one compromised domains and their rise and fall over time in the traffic that Cisco blocks due to increased bad reputation, at which point the threat actor(s) switch to using different compromised domains. Throughout this campaign the URI path -/b/728
 Hot Tags :
Security
Snort
advertising
Exploit
cdn
malvertising
Pack
redirection
iframe
Hot Tags :
Security
Snort
advertising
Exploit
cdn
malvertising
Pack
redirection
iframe