































In enterprise networks, standard and extended ACLs (Access Control Lists) are used to filter traffic and protect the network from unauthorized access and spoofing attacks. However, traditional ACLs have a limitation - they do not keep track of the connection state. This means that if someone inside the network sends traffic to the Internet, it becomes difficult to safely allow the returning traffic back into the network without compromising network security. Traditional ACLs also consume a lot of memory because they require multiple static inbound and outbound flow combinations with multiple match criteria. To address this issue, Cisco has introduced the Reflexive ACL feature on Catalyst 9000 series switches starting from IOS-XE 17.10.1 release. This feature provides a stateful behavior to the Access List, enhancing network security and efficiency.
Access List
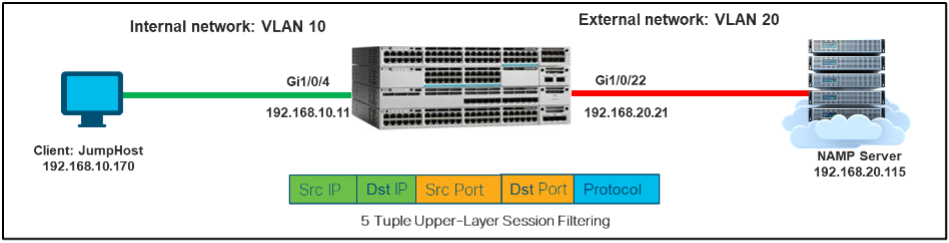
Now, let's examine the network layout shown above. Imagine there are two networks: the Internal network (192.168.10.0) and the External network (192.168.20.0). Let's consider a situation where a device within the Internal network needs to connect to a server in the External network, and another device wants to access the server via the web.
To achieve this, we need to set up extended access lists. These access lists should be configured on the inbound interface of the border switch. Their purpose is to allow the "web" traffic from the server to reach the device in the Internal network.
Switch#conf t
ip access-list extended ACL_inbound
permit tcp host 192.168.10.170 host 192.168.20.115 eq www
deny ip any any
end
Switch#conf t
interface GigabitEthernet1/0/4
no switchport
ip address 192.168.10.11 255.255.255.0
end
Switch#conf t
int gi1/0/22
no switchport
ip address 192.168.20.21 255.255.255.0
ip access-group ACL_inbound in
end
The above configured ACL being applied to one host in the network seems fine. But one thing to consider, it will not be possible on a large-scale network. In order to connect to the Web server or perform a simple ping, you need to allow all WWW/ICMP replies to come back to these devices or services. These statements are always active, so a hacker can use them to launch a denial of service (DoS) spoofing attack on the network. You should include them in the extended ACL, which will help increase the TCAM memory that the switch can use.
Reflexive Access List
The reflexive ACL works in a unique way by allowing two-way filtering. It allows the returning traffic from connections that started from within the network to come back in. Reflective ACLs deny traffic that originates from outside the network and tries to connect to internal resources.
Whenever an internal device establishes a connection with the outside world, a temporary entry is created. This temporary entry allows the returning traffic for that session to pass through the border switch and creates temporary entries in the inbound filter.
Reflexive ACL Configuration as an example:
!Configure reflexive access list on outbound interface!
Switch#conf t
ip access-list extended ACL_out
permit tcp host 192.168.10.170 host 192.168.20.115 eq www reflect R1 timeout 100
!where R1 is the name of the reflexive access list!
!timeout of 100 is to put a timer on the temporary entries created!
deny ip any any
end
Switch#conf t
int g1/0/4
ip address 192.168.10.11 255.255.255.0
ip access-group ACL_out in
end
!Configure reflexive access list on inbound interface!
Switch#conf t
ip access-list extended ACL_in
evaluate R1
deny ip any any
end
Switch#conf t
int g1/0/22
ip address 192.168.20.21 255.255.255.0
ip access-group ACL_in in
end
When using ACL with "reflect" ACL, temporary entries are created to allow reverse traffic. These entries will only be activated if there is an ACL with an "evaluate" ACL applied in the opposite direction.
Reflexive ACL offers several advantages for enterprise networks. It provides stateful filtering, which is more difficult to fake because multiple filter criteria must be met before a packet is allowed. It also uses temporary filters that are removed once a session is finished, reducing the time window for potential hacker attacks.
There are additional benefits to using Reflexive Access-Lists. It is easy to implement and configure, while providing greater control over external traffic due to its stateful nature. This feature is available on all Catalyst 9000 switches with IOS-XE 17.10.1 (and newer) installed.
If you have more questions about Cisco Routers and Cisco Switches. You could contact us www.hi-network.com (Email: info@hi-network.com)
 Hot Tags :
switches
Hot Tags :
switches