































There are many advantages in outsourcing functions to specialist providers that can supply services at lower cost and with more functionality than could be supplied in-house. However, companies should be aware that when buying services, you may also be buying risk. Organisations that have successfully implemented strategies to reduce the probability of experiencing a breach, and to decrease the time required to discover and remediate breaches, may still encounter embarrassing public breaches via third parties. Within the past two weeks, we have seen two examples of companies having their websites defaced apparently due to security lapses in service providers.
that when buying services, you may also be buying risk. Organisations that have successfully implemented strategies to reduce the probability of experiencing a breach, and to decrease the time required to discover and remediate breaches, may still encounter embarrassing public breaches via third parties. Within the past two weeks, we have seen two examples of companies having their websites defaced apparently due to security lapses in service providers.
The OpenSSL project is a community of volunteers developing commonly used cryptographic software. Trust and reputation are important to all organisations, but are vital to suppliers of cryptography. Hence, it caused great concern when the project's website was reported as being defaced on 29 December, even though the cryptographic source code remained unaffected [1]. The breach was reportedly caused by the use of insecure passwords by the hosting provider that allowed an attacker to make unauthorised changes to the project's webserver. Further details can be found on Richard Gold's blog post.
The Hacker News recently reported a similar attack where an attacker redirected the Tajikstan websites of Yahoo, Twitter, Amazon and Google [2]. In this incident, the attacker reportedly used a directory traversal vulnerability to access the control panel of the DNS registrar and used this to gain control of the domains. At this point, the attacker was able to change the master DNS record to direct the domain name to any server that the attacker desired. Cisco's SIO data suggests that the DNS record for google.com.tj was changed shortly before 13:00 GMT on 4 January, two days before the attack was publicised.
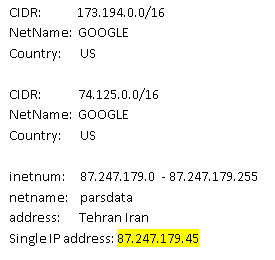
Whois data for IP addresses recorded for google.com.tj on 4 January.
We have previously written about similar attacks leading to high-profile websites being compromised [3]. It appears that compromising registrars and hosting providers to take control of organisations' websites remains a fruitful technique within the attackers' toolkit.
Organisations should prioritise their own network security to ensure that their in-house systems are resistant to attack. However, organisations that are at high risk of attack may wish to consider the security of third parties that deliver outsourced services. These suppliers may provide an attacker with a mechanism by which a target organisation can be embarrassed with a high-profile compromise even though the target has a high level of security in place.
To protect against such attacks organisations should ensure that their domain names are locked against malicious transfer and verify that the network security procedures of their hosting provider and domain registrar meet their security requirements. It is also important to plan for the possibility of a domain name or website becoming compromised. Organisations should ensure that they are able to swiftly detect unauthorised changes to their DNS records or web pages, and have in place a well-rehearsed plan or playbook to remediate the compromise as soon as possible.
The security of third-party providers is, by definition, outside of the control of their customers' security managers. However, by raising their concerns and asking for security assurances, security managers can help ensure that providers prioritise security and reduce risks. High-profile attacks such as these remain rare, but by seeking to manage external risk and by preparing contingency plans organisations can help to ensure that incidents such as these become even rarer.
References.
1. OpenSSL news report 2014-01-03. http://www.openssl.org/news/secadv_hack.txt
2. "Tajikistan's Domain Registrar hacked; Google, Yahoo, Twitter, Amazon also defaced", The Hacker News, 2013-01-06. http://thehackernews.com/2014/01/Tajikistan-Google-Twitter-hacked-Domain-Registrar.html
3. "Syrian Electronic Army Continues Spree: Cracks New York Times, Twitter and Huffington Post", J. Schultz, Cisco Blog, 2013-08-27. https://blogs.cisco.com/security/syrian-electronic-army-continues-spree-cracks-new-york-times-twitter-huffington-post/
Andrew Tsonchev contributed to this post.
 Hot Tags :
TRAC
dns
Hot Tags :
TRAC
dns