


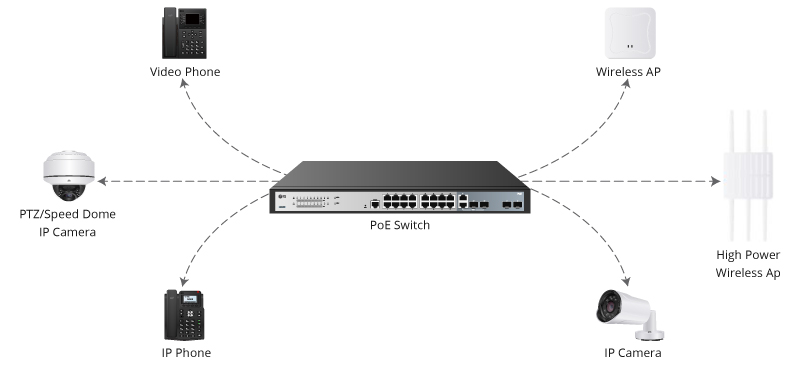

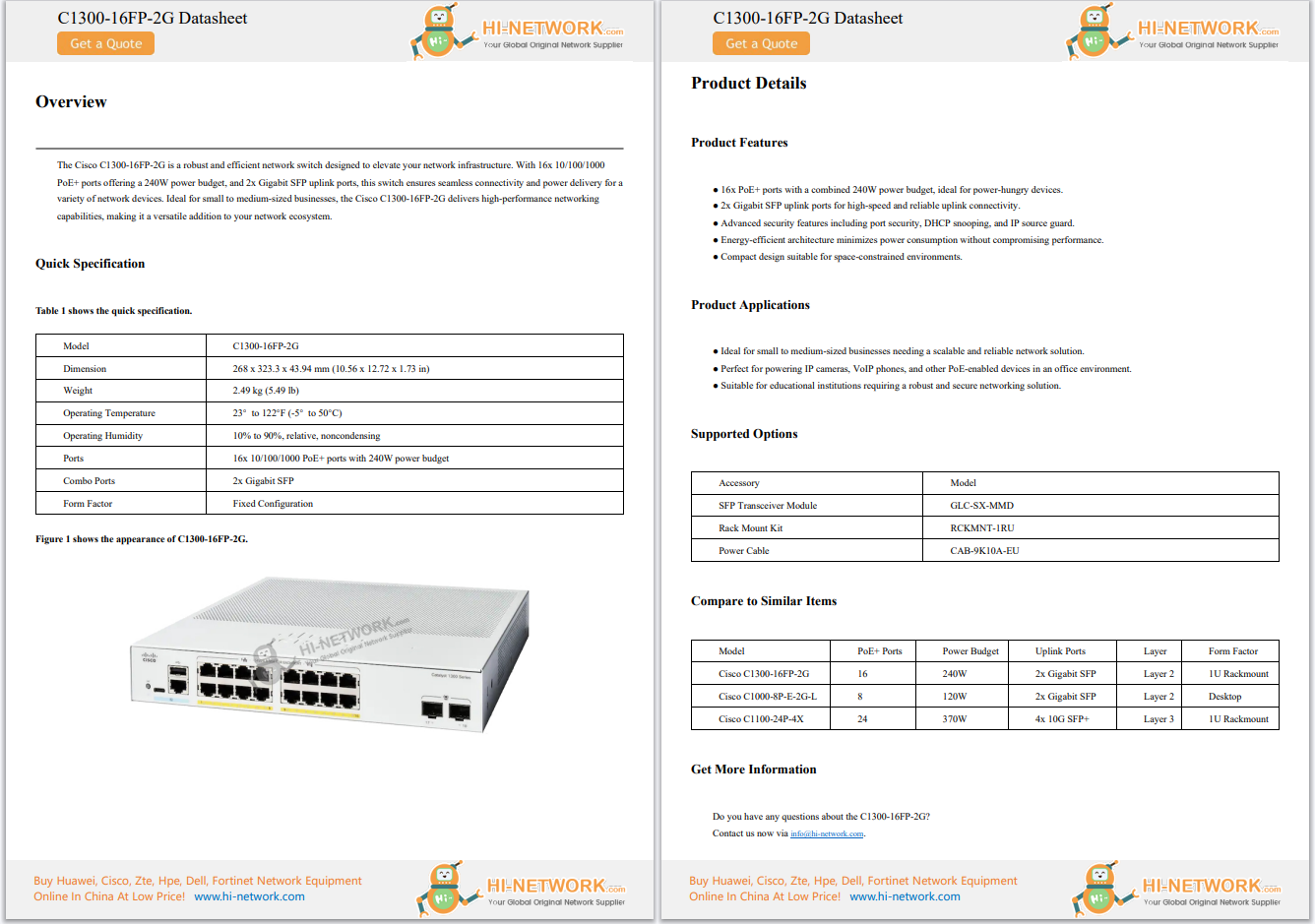






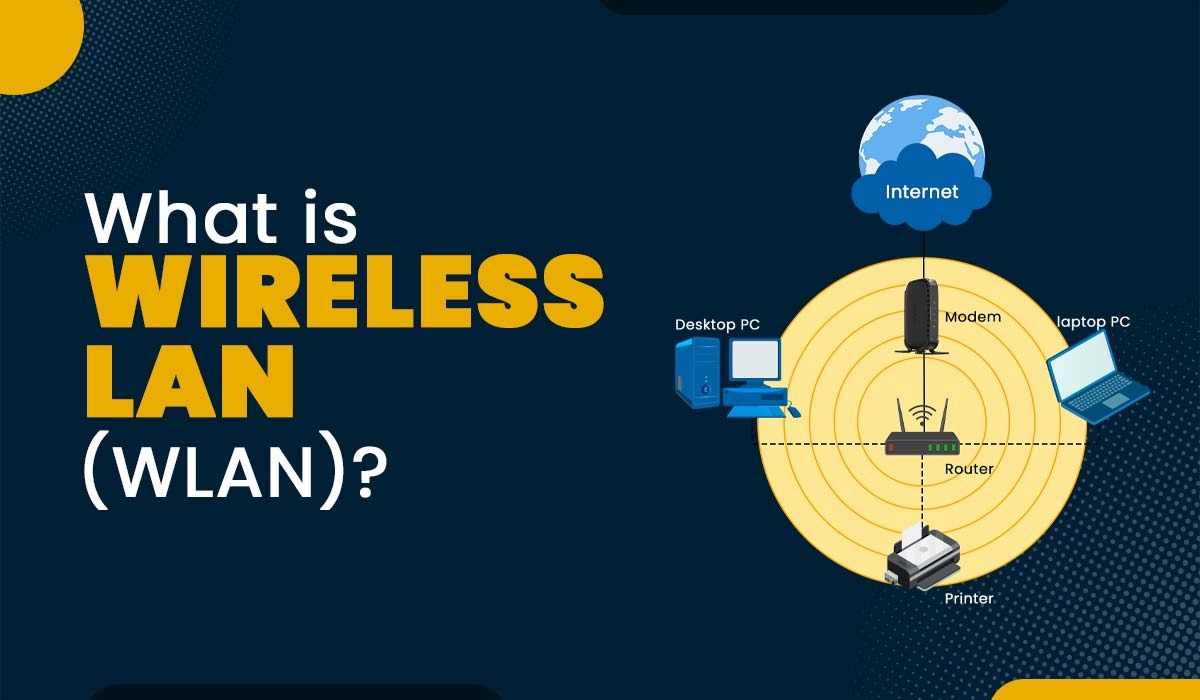






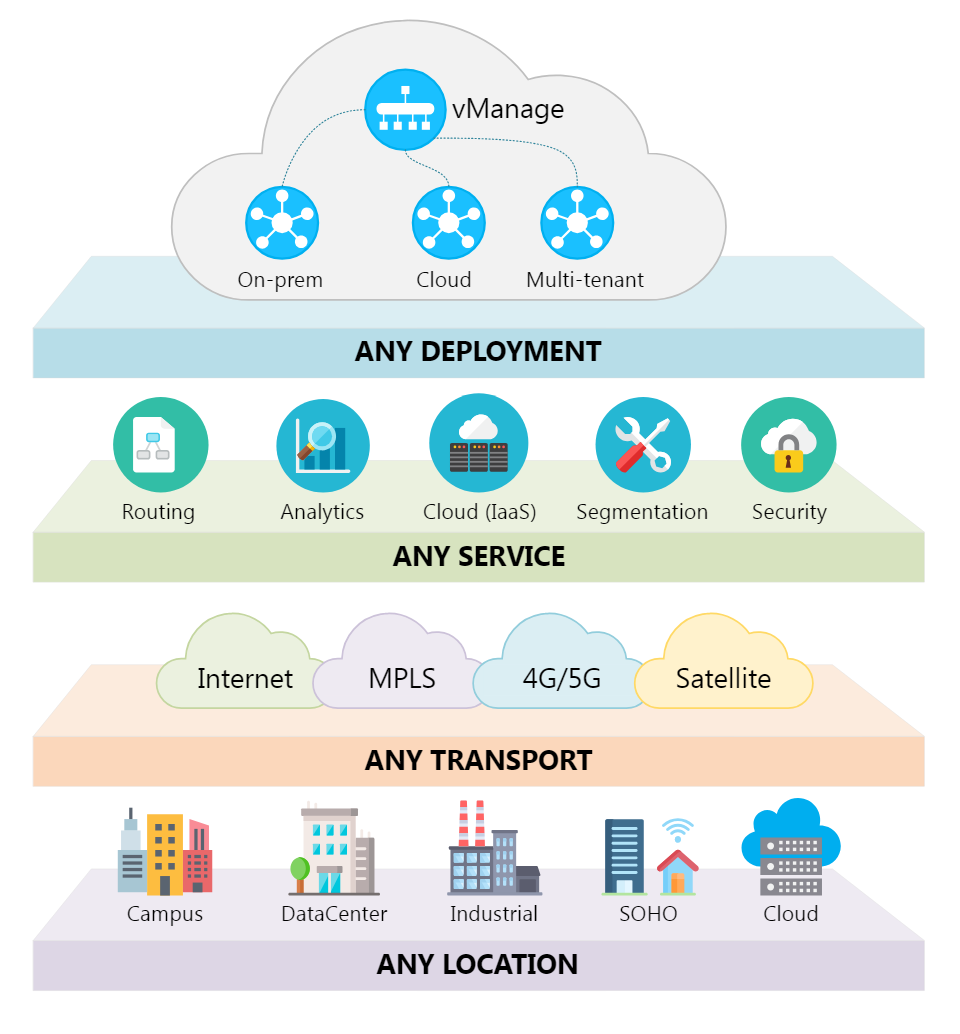
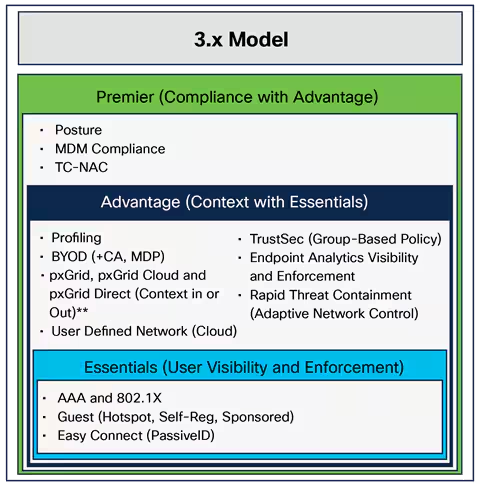

Data is growing at an astonishing rate. Trends like cloud, IoT and digitization are imposing higher demands on how data is managed, transported, backed up and restored. Increased business dependence on IT means downtime has more m...

The way that Jaipur looks at it, every few centuries a city needs an upgrade. As one of the biggest tourist destinations in India, Jaipur wanted to transform itself into a more modern, digital city to handle the needs of the peop...

In late August we began to detect malicious Microsoft Word documents that contained VisualBasic (VB) macro code and the code appeared to be triggering when the document was opened. However, the documents did not contain any of the...

During the last few years we have witnessed how the cyber security threat landscape has evolved. The emergence of the Internet of Things combined with recent events have profoundly changed how we protect our systems and people, an...

On October 4, 2016, powerful Hurricane Matthew crashed into the southwestern tip of Haiti as a category 4 storm with 145 mph winds, destroying homes, major bridges and infrastructure and flooding communities. Next Matthew mo...

Vulnerability Discovered by Tyler Bohan and Cory Duplantis of Cisco Talos Talos has identified an exploitable out-of-bounds write vulnerability in the ELF Section Header parsing functionality of Hopper (TALOS-2016-0222/C...

#CiscoChampion Radio is a podcast series by Cisco Champions as technologists. Today we're discussing Cisco CloudCenter. Get the Podcast Listen to this episode Download this episode (right-click on the episode's download bu...

The digital transformation of Argentina has begun -and Cisco is at the forefront of the change. First though, it's important to note that, Latin America faces some daunting statistics: 21 million Latin Americans will be unemployed...

Yesterday, the US Environmental Protection Agency (EPA) presented Cisco Systems with a Green Power Partner of the Year award. The Green Power Leadership Awards recognize Green Power Partners for their leadership, overall renewable...

Vulnerability discovered by Aleksandar Nikolic of Talos. Talos has identified an information disclosure vulnerability in Foxit PDF Reader (TALOS-2016-0201/CVE-2016-8334). A wrongly bounded call to `memcpy`, while parsing jbig...

Everyone knows that Software Defined Networking (SDN) and Network Function Virtualization (NFV) technologies are key to future Service Provider(SP) success. But how to get there is something that most service providers are struggl...

In April we covered the description of Email Spoofing using Microsoft Outlook, but what about detecting and mitigating it on the Mail Transfer Agent (MTA)? There are multiple technologies that have attempted to address the issues ...