


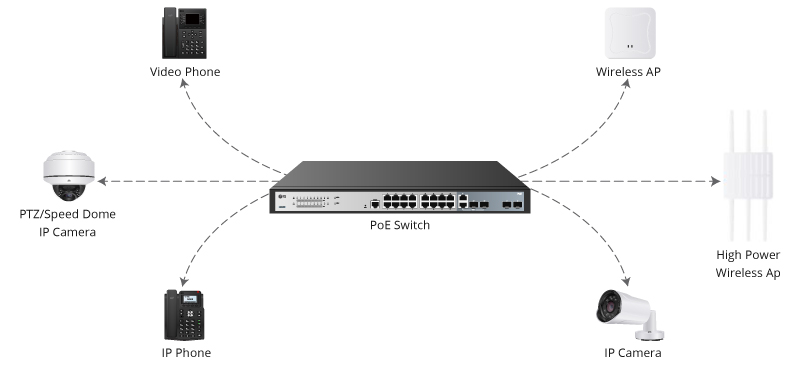







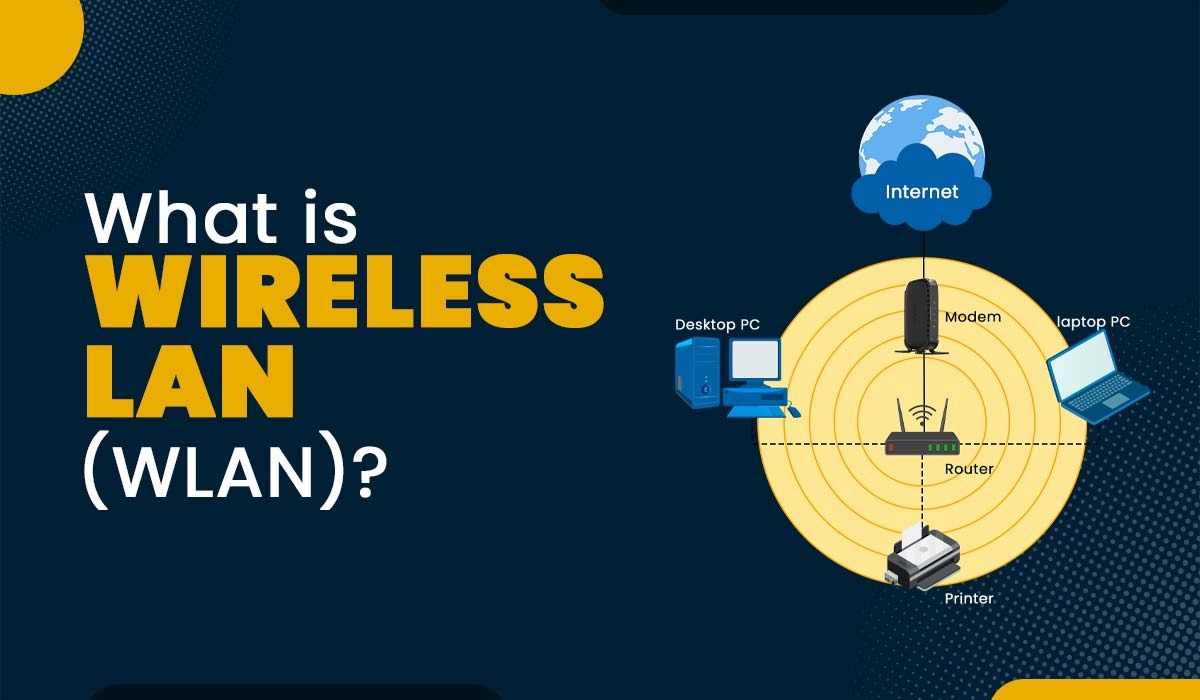







For many government agencies, cybersecurity can be an afterthought, a one-off, single product they add on after the fact to meet regulation or protect from basic hacks. What these agencies don't realize is that cybersecurity isn't...

Next week the Open Networking User Group meets for its fall conference in New York City. I am looking forward to learning how the SDN landscape is evolving and what is top of mind for IT architects and business leaders. One hot to...

Elianna Goldstein is a Cisco Intern who shared her story with us this summer before returning to school. We hope your semester is amazing, Elianna! For two summers in a row, I worked at small non-profits and volunteered, as I sou...

Most C-suite leaders think about cybersecurity as a way to stop threats. But in today's intensely competitive digital economy they should be thinking about cybersecurity as a strategic advantage that not only protects business val...

How often do you attend meetings that start late due to technology issues? According to Ovum, the average delay is 10 minutes and 40 seconds. When technology isn't easy to use, it impacts productivity and can cost millions in lost...

The nation of Iraq is frequently in the news, but up until now not because of its ultra-modern IP and optical network. This week we announced that Cisco is playing a key role to restore and rebuild the Iraqi National Backbone, a m...

LikeRenee Pattonwho isGearing up for EDUCAUSE 2016, I am equally thrilled to be co-presenting with BruceMaas and BobTurner from the University of Wisconsin -Madison. Our session, Effective Threat Detection: The Key to Constra...

This post was authored by Edmund Brumaghin and Yves Younan Summary Ransomware has become increasingly prevalent in the industry, and in many cases, unless there is a publicly released decryptor available, there is often not an eas...

Over the past few years, location-based services such as Google Maps, Yelp, or OpenTable have become pervasive in our lives. In fact, 70 percent of smart phone customers now use location-based services. But similar, location-based...

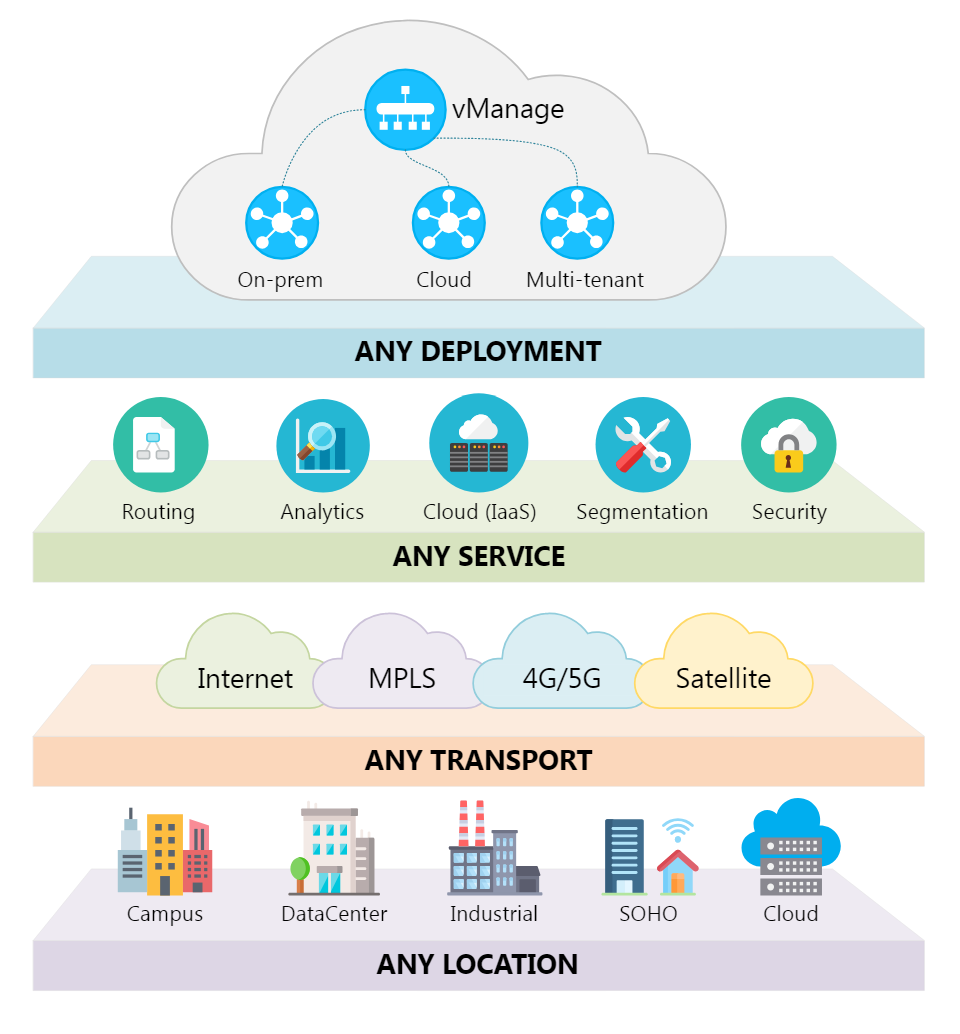
Submitted by Kelsey Kusterer Ziser, the Editor of Upskill U at Light Reading As service providers migrate traditional networks to virtualized networks, it's no longer enough to only secure the perimeter. Threats from within the ne...

"The only constant is change." It's an adage that goes back 2500 years to the Greek philosopher Heraclitus. But never has it been as true as it is today. Technology adoption is growing exponentially, driving change at a dizzying p...

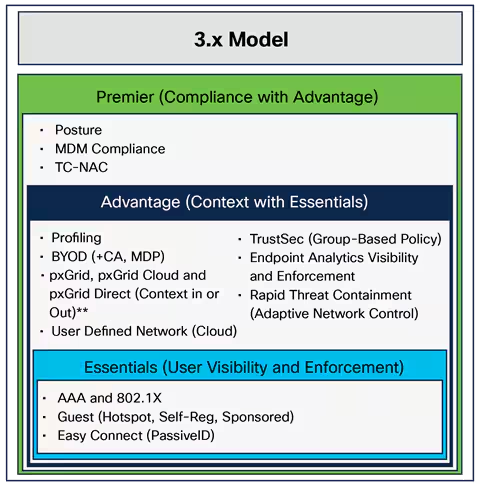
Based on the cybersecurity news proliferating in the mainstream media today -from ransomware incidents to data breaches of massive proportions -it has become clear that organizations need to put security mechanisms in place to pro...