


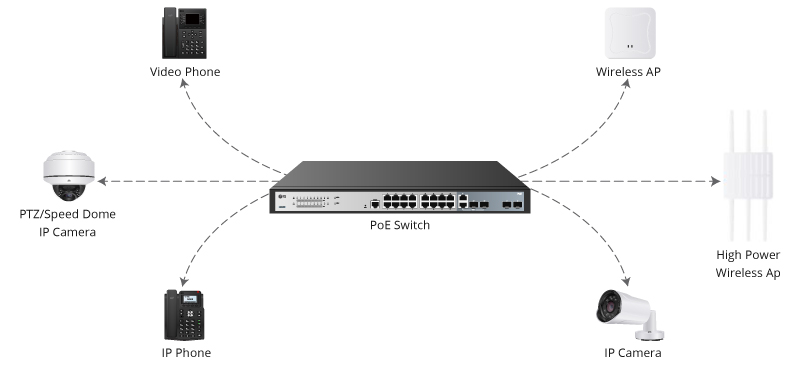







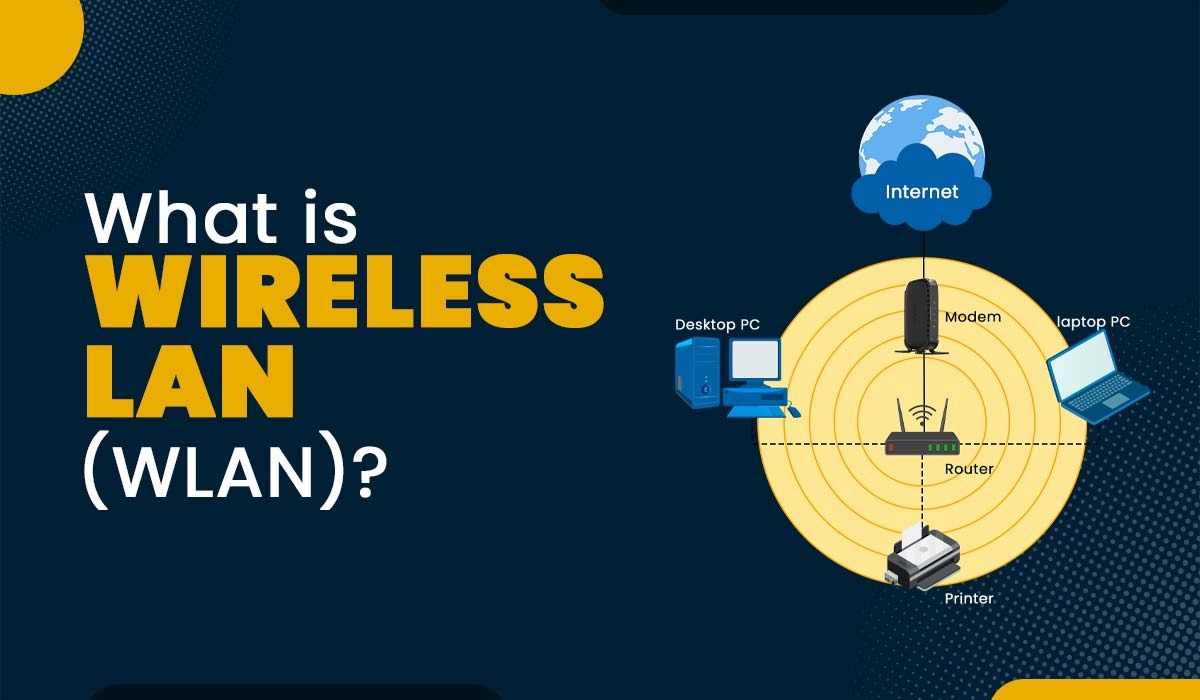
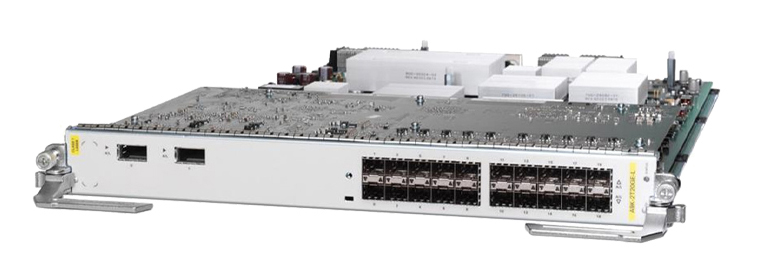






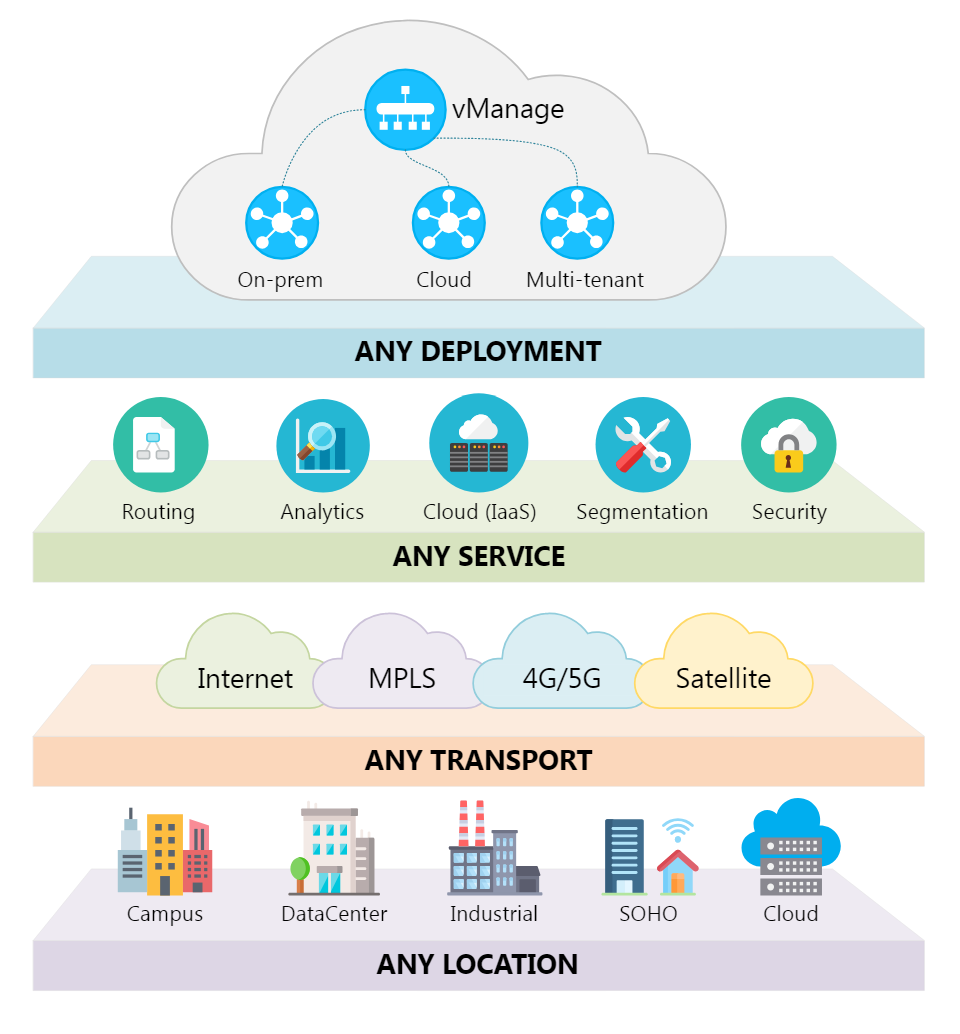
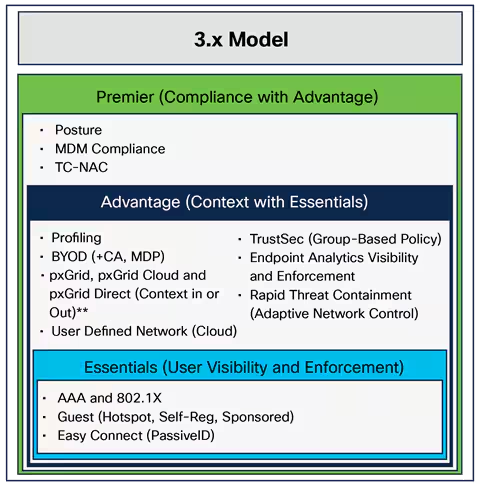

We've talked about how Cisco is helping network operators leverage the tools of the data center to better manage the network. To show a real world example of this a few weeks back Cisco and Ansible teamed up for SDx Demo Friday. W...

Just over a year ago Cisco announced the general availability of APIC-EM (#APICEM), a software defined networking (SDN) platform for the enterprise branch, campus and WAN. In just over 12 months, we have seen over 1400 enterprise ...

What if the world's leading mobile devices communicated at a deeper, more trusting level with the world's leading corporate networks? That was the question that Apple and Cisco asked themselves when they announced their new partne...

Over the past few years, I have seen IT organizations adopt cloud in very different ways. Some organizations prefer to standardize their cloud infrastructure to drive efficiencies in their data centers. As a result, they eventuall...

I've always had compassion for the plight of many in Africa. I think it started from me being overly sensitive at a young age and taking the old dinner table saying "finish your food, there are starving children in Africa" to hear...

I recently had the pleasure of joining a twitter#CiscoChat co-hosted by @CiscoServices and Zeus Kerravala @zkerravala of ZK Research. We started the chat to debate the pros and cons of software support, but as we dove into the cos...

Effective security is simple, open, and automated. In the last blog, I described several efforts by Cisco to pursue simplicity. Now let's talk about how we are executing on the open part. Openness is about playing well...

This blog post was guest-written by Kimberly Bowman, Marketing and CommunicationsSpecialist, Cisco Community Relations. It is the start of the annual holiday season. In the United States, we have a day for getting deals (Black Fri...

Utilities across the globe are telling us that cybersecurity risks and protecting data from intrusion and manipulation are among their highest concerns. To shed light on this critical topic, we are hosting a#CiscoChat to learn how...

This post authored by Nick Biasini and Edmund Brumaghin with contributions from Sean Baird and Andrew Windsor. Executive Summary Talos is continuously analyzing email based malware always looking at how adversaries change and the ...

The Chinese calendar calls 2016 the year of the monkey, but looking back on our industry these past 11 months, I would call it the year of the customer. Why? Because as digital disruption takes hold and transforms the way we do bu...

Responsible disclosure of vulnerabilities is a key aspect of security research. Often, the difficulty in responsible disclosure is balancing competing interests -assisting a vendor with patching their product and notifying the gen...