


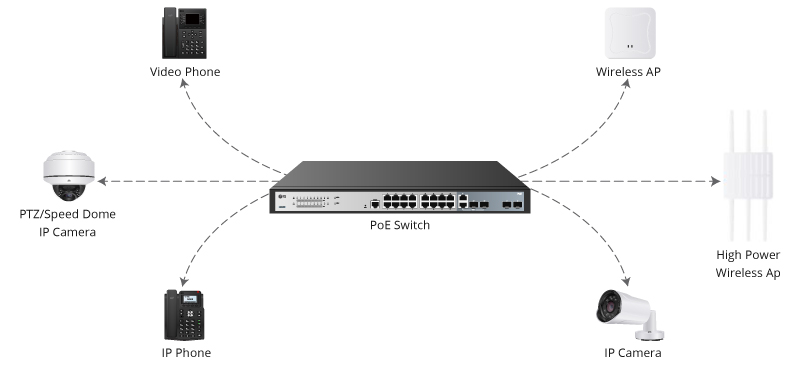

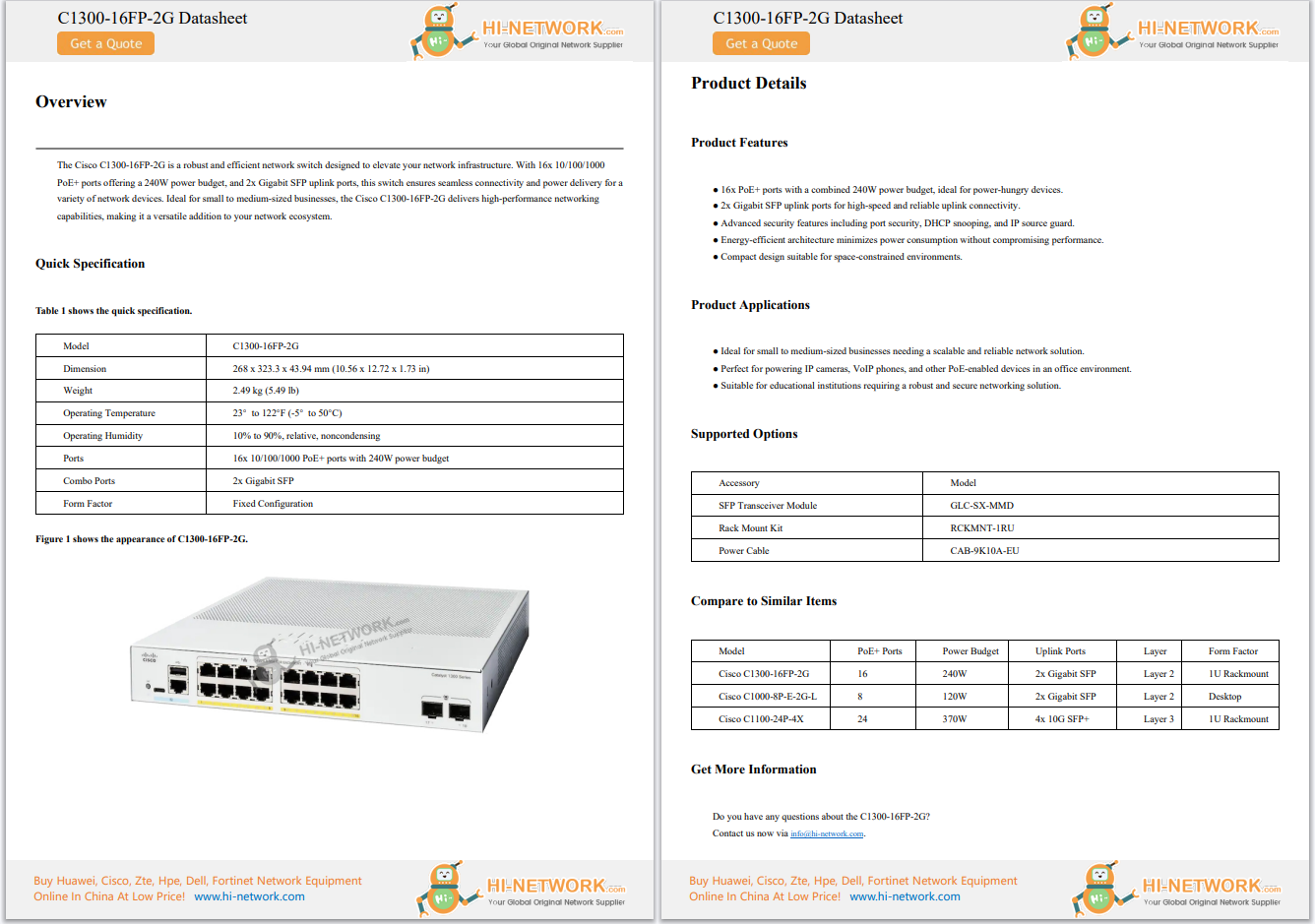













When you start working at Cisco, you quickly realize folks here have their own language. Sure, there's tech lingo and acronyms galore, but it goes much deeper than that. You hear, quite a bit, in those conversations that people h...

In our highly connected business environments, the need to respond to the inevitable security breach is on the minds of every CISO. An increasing number of organizations rely on the services of a Managed Detection and Respon...

Did you know Pokemon Go set the record for the Apple App Store downloads in the first week? Not only that, it has gone on to break five Guinness World Records: Most revenue grossed by a mobile game in the first month Mos...

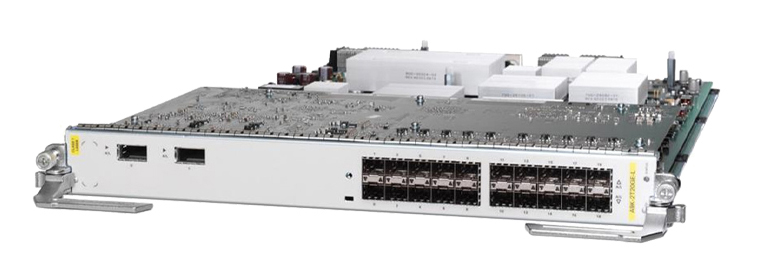
Virtualization is an overloaded word. Originally it was used to describe a form of hardware emulation, but these days it appears that any form of software abstraction is called "virtualization". In the context of the CMTS the term...

Part 1: What does it take to win in an OTT world? In this blog trilogy, I will try to shed some light on one of the more intriguing topics in the video industry-OTT video. I will discuss the reality of OTT video, the service prov...

In my previous post, I shared the challenges of innovating within a large enterprise. I also shared some solutions, including our creation of Startup//Cisco-our grassroots effort to accelerate startup up DNA within Cisco. Since la...

When it comes to over-the-top (OTT) video distribution, we are seeing many of our customers opt for a multi-DRM approach. This means utilizing the DRM client that is pre-integrated into the viewing platform instead of installing a...

I need to preface this blog with a full disclosure statement. I love shopping! And apparently I am not alone in my affinity for all things retail. Let's face it, many people enjoy the thrill of acquiring a new "bright shiny t...

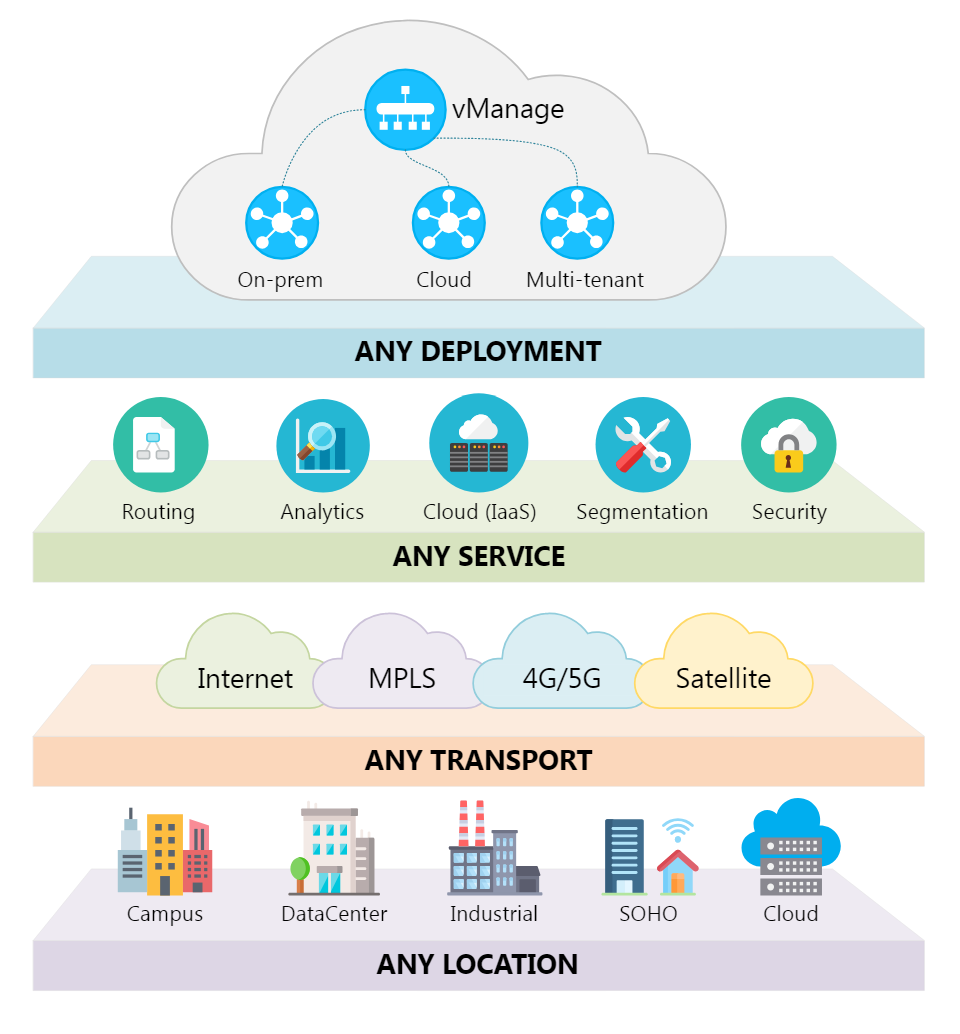
Three Keys to Success: Preparing your mobile network for 5G. Learn more: Download our new 5G ebook While much of the focus in the press on 5G has been around the definition of a new radio interface and the architecture to supp...

Everyday, hackers and cybercriminals are infiltrating networks. And they are especially interested in healthcare. That's because stolen medical records are profitable, selling up to 10 times more than credit card numbers on the bl...

Project FIRST is lead by Angel M. Villegas. This post is authored by Holger Unterbrink. Talos is pleased to announce the release of the Function Identification and Recovery Signature Tool (FIRST). It is an open-source framework th...

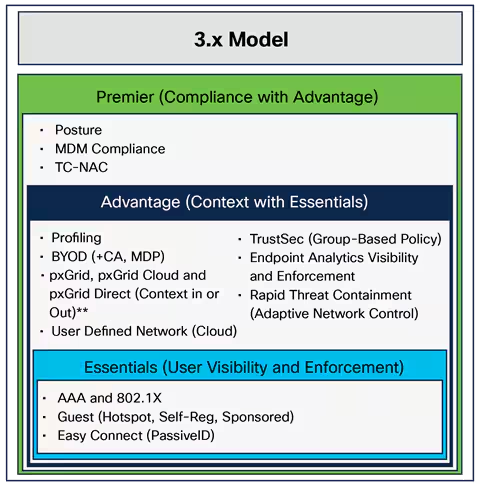
In the world of cybersecurity, many organizations have implemented some version of the 'identify, protect, detect, respond, recover' framework proposed by United States National Institute of Standards and Technology (NIST). Underp...