


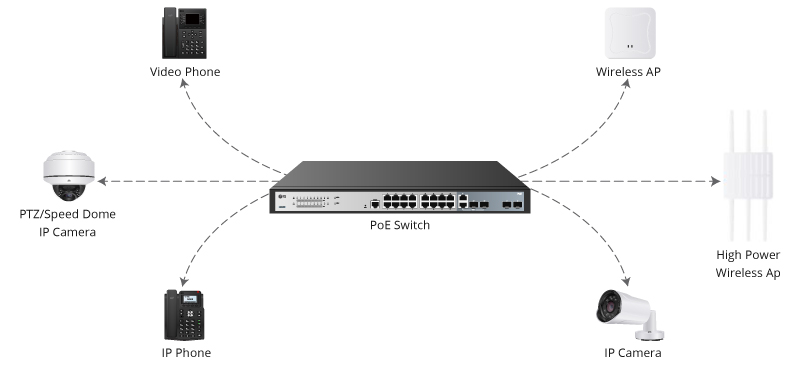

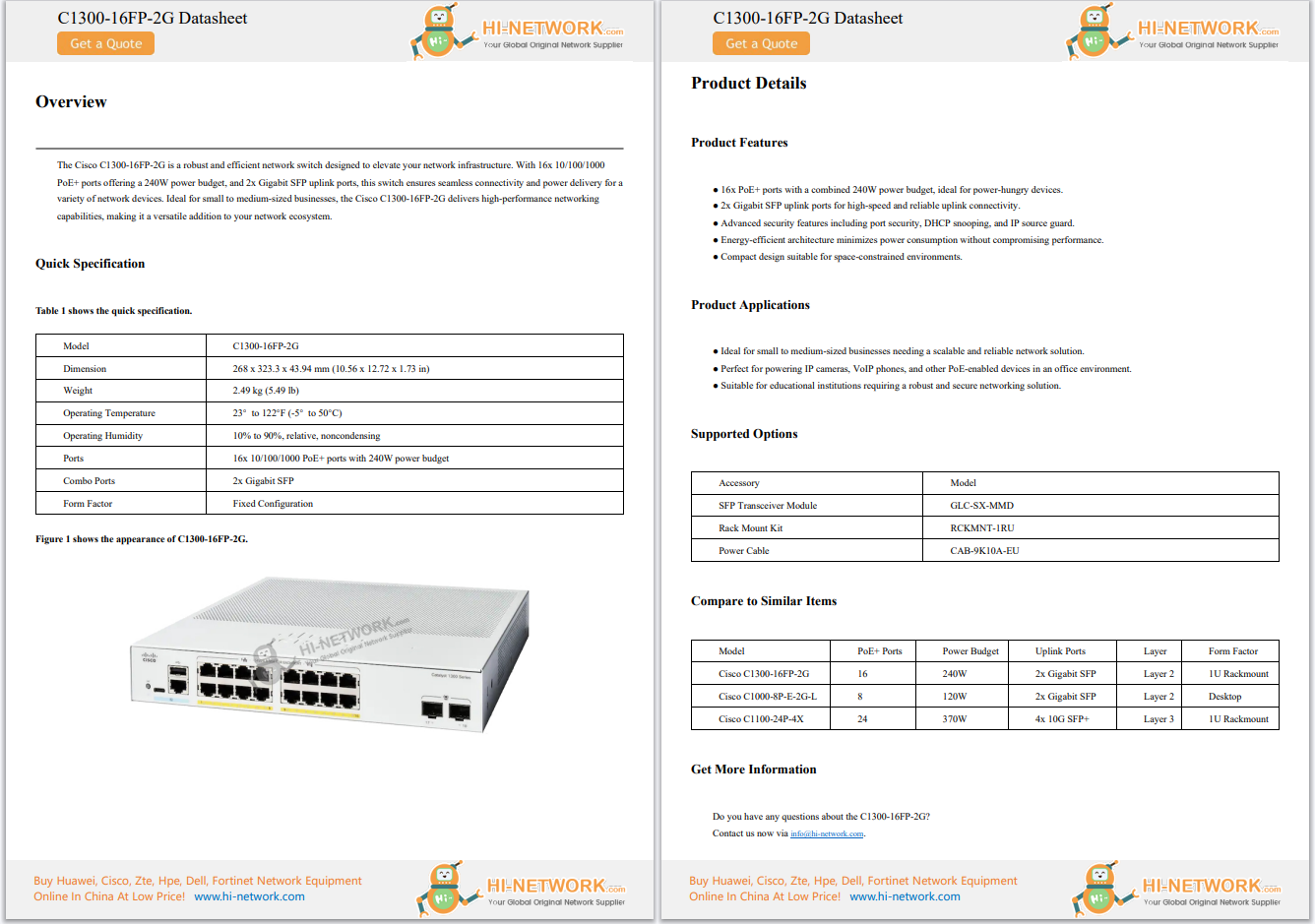
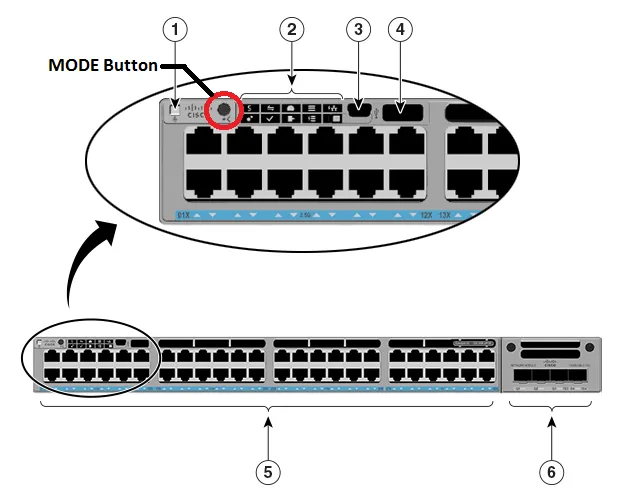




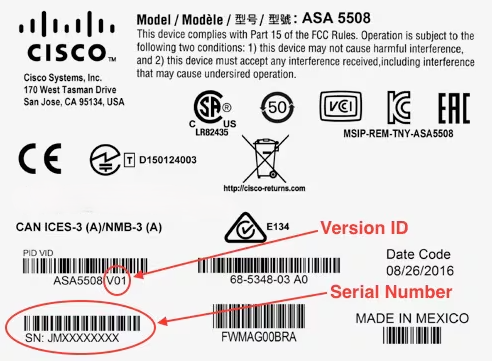


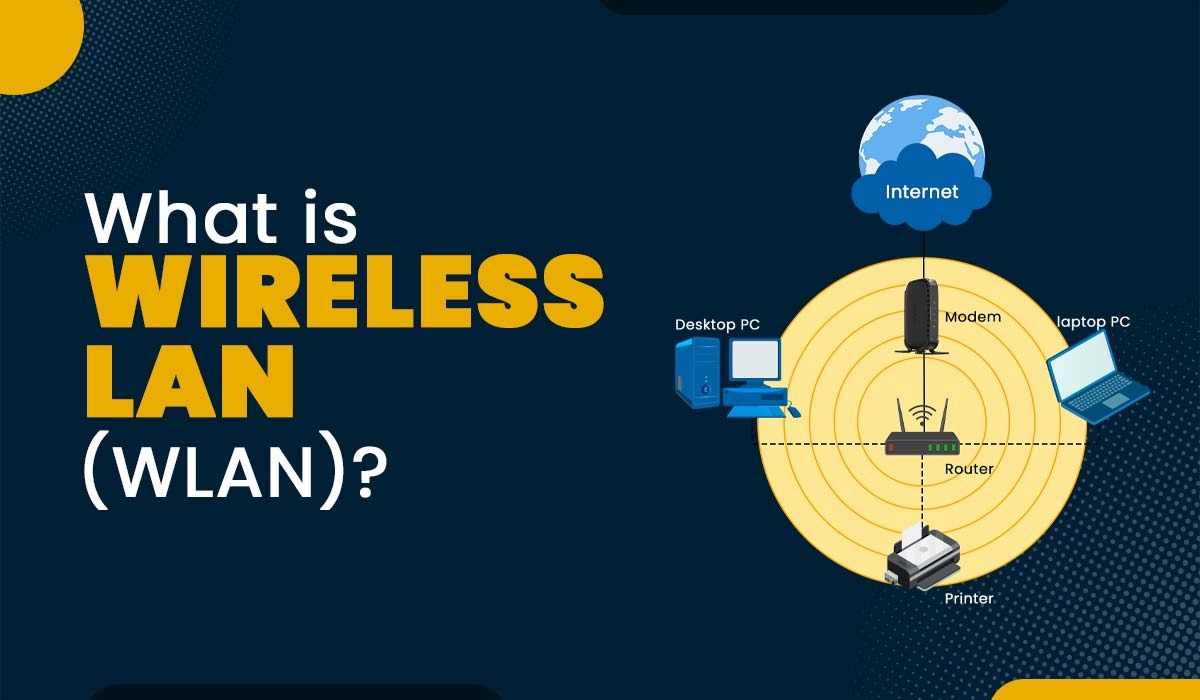







When I ask the question of Healthcare CIOs and CISOs "What keeps you up at night?" one of the most common answers I receive -after the usual jokes about indigestion, or the snoring spouse, is the problem of what to do about securi...

Are you looking to better understand the current landscape of industrial security? What about best overall practices for securing your plant floor? Or do you want to understand what technology can help you secure your operations f...

When I was in 8thgrade, I adopted a child...a sponsor child I mean! Her name was Blessing, and she was a young girl who was living in an orphanage in Kenya and needed help. Her mother died of AIDS when she was born and her father ...

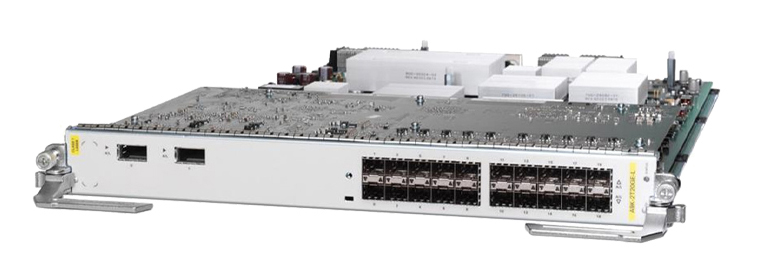
This post was written by guest blogger Yuji Suzuki, Manager of Japan Manufacturing Operations. Think of a large piece of Cisco equipment, like a carrier-class router. Now picture the product's shipping carton: it's a side car...

I promised a follow up in my recent blog about Facebook's new Bryce Canyon storage platform. While the title of this blog may sound like it questions the new platform's capabilities. It like the previous blog aims to help you unde...

It's April, and that means it's time to pack back out to Las Vegas for the National Association of Broadcasters convention, scheduled for the last week of the month. And because we've lots to talk about, and you probably have limi...

The Marketing Velocity Live Event (Chicago, April 25-27) is just around the corner. To say I'm excited is an understatement. This is our 10thyear conducting this invitation-only event that challenges and educates our partners abou...

Late last year, I compared Cisco's S3260 Storage Server to Amazon's S3 service. The results shocked a lot of people and spurred a lot comments on the blog. It's worth repeating from the last conversation on this topic that there ...

On Friday, April 14, the actor group identifying itself as the Shadow Brokers released new information containing exploits for vulnerabilities that affect various versions of Microsoft Windows as well as applications such as Lotus...

As more and more businesses make the shift to digital, questions of cybersecurity continue to arise. This is especially true in industries that have a lot at stake - industries like financial services. As digital transformation ra...

Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 7 and April 14. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the ...

Over the past week, information regarding a serious zero-day vulnerability (CVE-2017-0199) in Microsoft Office was publically disclosed. Since learning of this flaw, Talos has been actively investigating the issue. Preliminary rep...