


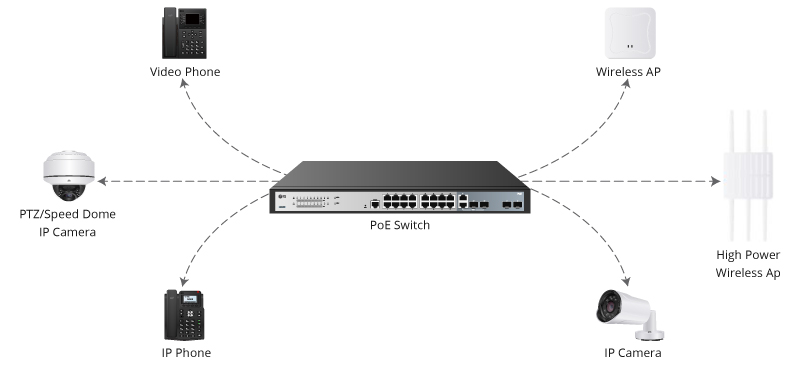







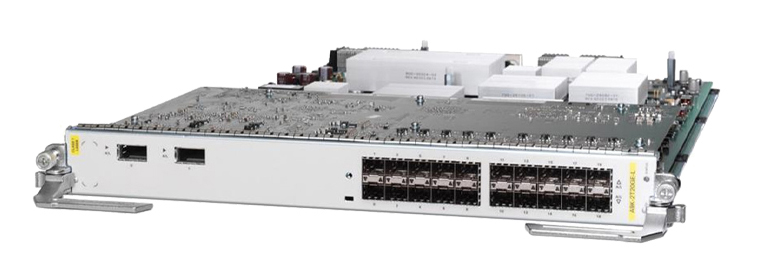






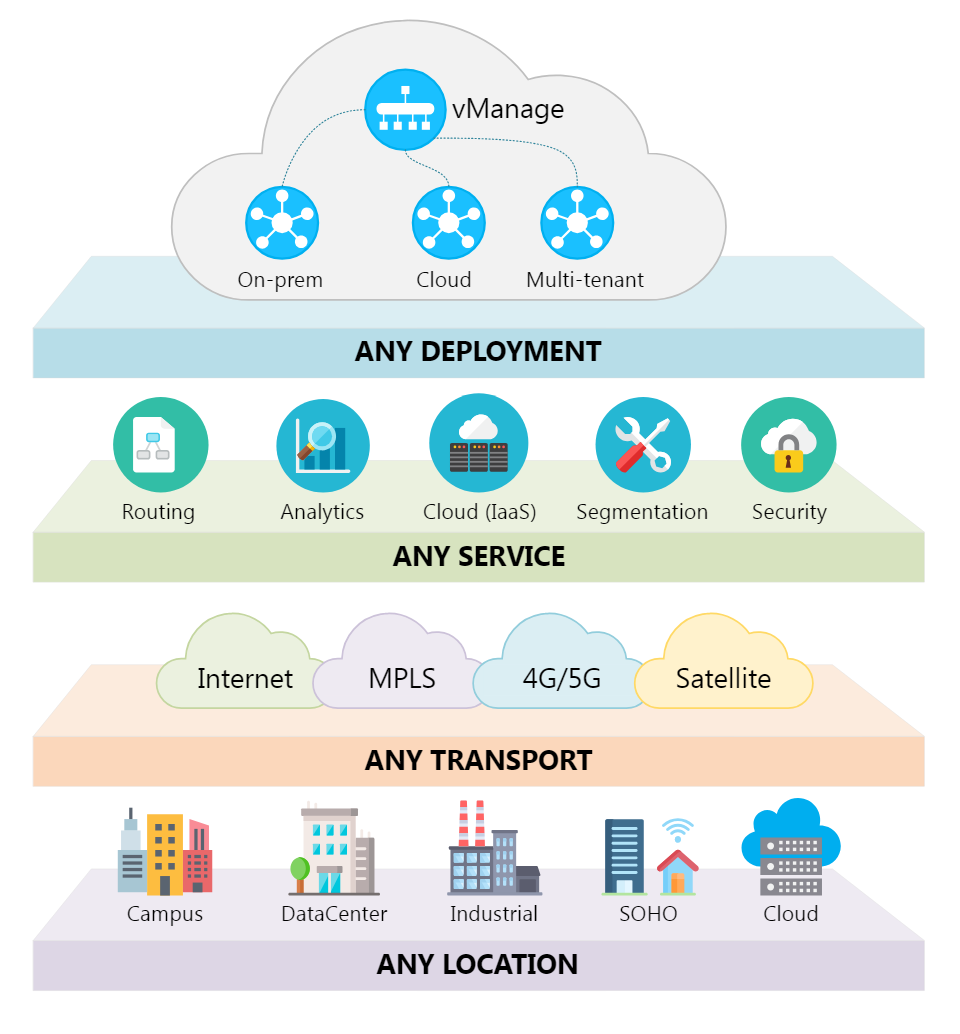
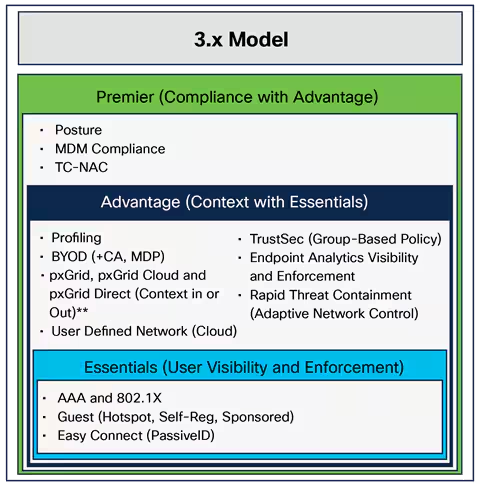

Cisco Threat Responseis built upon a collection of APIs; which can be used to integrate your Cisco and third-party security products, automate the incident response process and manage threat intelligence and security context data ...

Post authored byNick Biasini. Executive Summary As 2018 draws to a close, one technology has definitively left its mark on the year: cryptocurrencies. Digital currencies started the year out strong after a meteoric rise toward the...

Post authored byDavid LiebenbergandAndrew Williams. Executive Summary Through Cisco Talos

Cisco Collaboration is a partner-driven organization. 93% of our sales are through partners, a rarity in our industry these days. So what an honor to have our Webex redesign recognized as the overall Collaboration Product of the Y...

Ever wondered what Life at Cisco is like? Through the employee stories that appear on this blog twice a week throughout the year, that is exactly what we hope to share with you. A glimpse into what the culture, technology, a...

How to stop the

The Enterprise Networking team at Cisco got a great holiday present this year. CRN, the voice of the reseller channel, released its Products of the Year feature, and two of our most important initiatives won in their categories. T...

|Just|when you thought it could not get any better, the IETF Hackathon reached new heights, not just in number of participants or projects, but in meaningful contributions to the IETF community and the standardization process. Man...

Have|you|read Alice's Adventures in Wonderland? This is one of my favorite childhood books. The Cheshire Cat, known for its distinctive mischievous grin, and The Mad Hatter, an impolite hatter who lives in perpetual tea-...

The Holidays are upon us. I hope you have at least started on the gift acquisition project. Remember, shop small... Last week we were in Cancun for Cisco Live Latin America. It was an amazing experience. Every day we had various s...

Warning from Black Hat NOC Cisco Security helped secure the Black Hat Europe 2018 Network Operations Centre (NOC) for the second year; joining conference producer UBM and its other security partners RSA Security, Palo Alto Network...

Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Dec. 7 and Dec. 14. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the thr...