




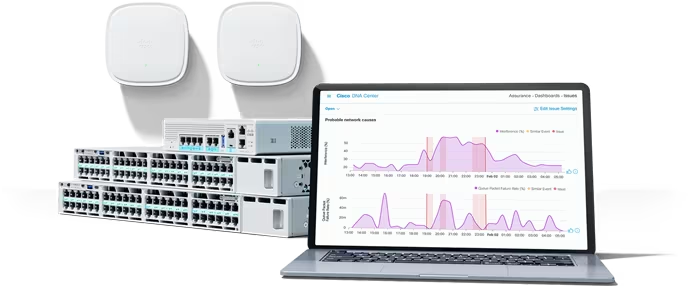
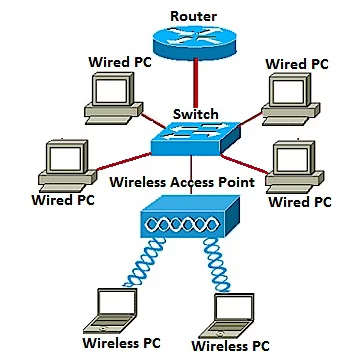



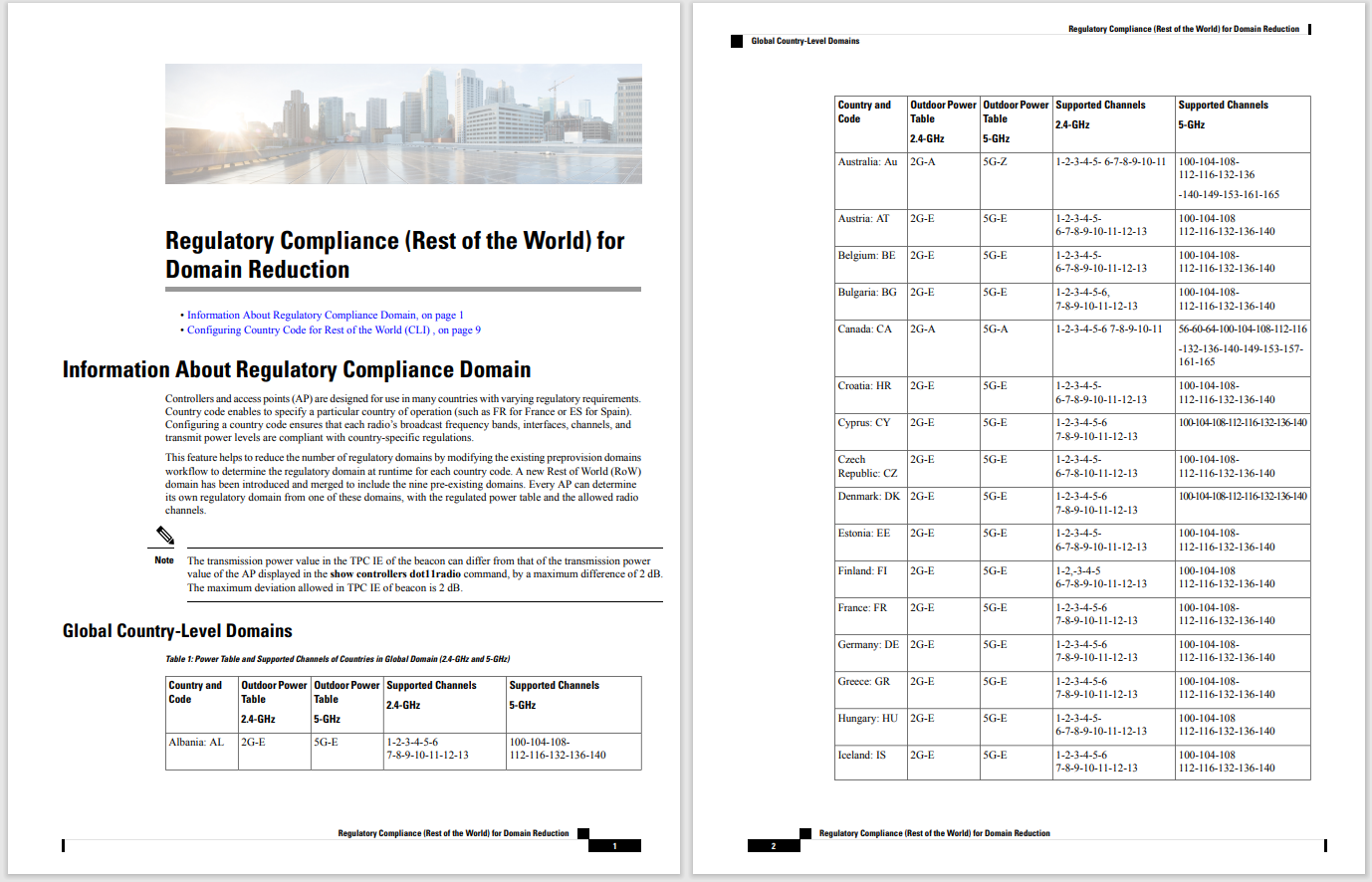
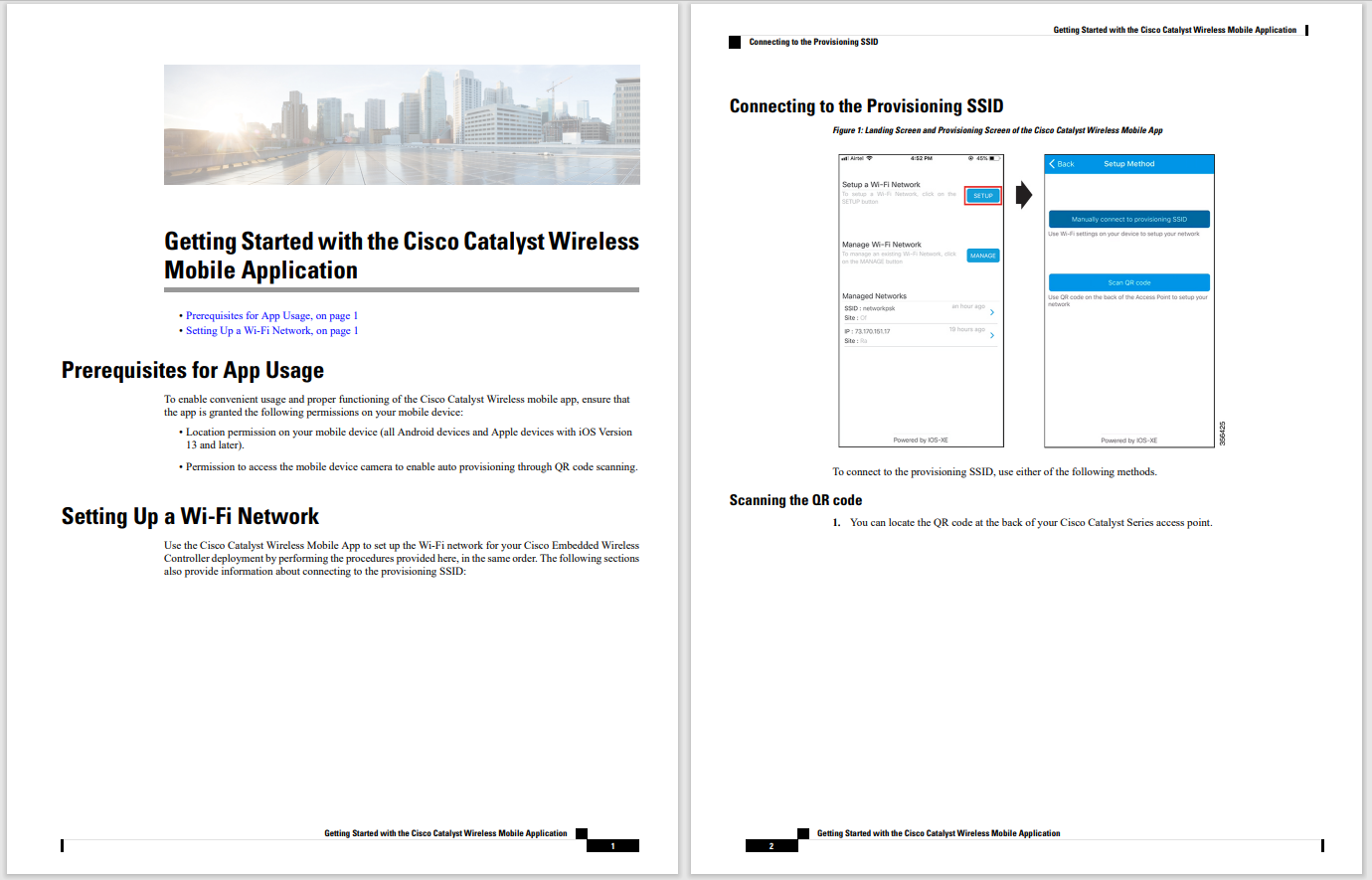














A show of hands: How many of us make completely rational choices every time, all the time? I'm waiting. Most of us do our homework before making major investments. When buying a home or a car, for example, we scrutinize our options to ensure they fit our needs and budgets. However, intangibles like style or appearance can creep in and affect our decision-making. The opinions of others, or fear of missing out, can sway us from good choices too. For many, this applies to cyber investments as well.
And then there's decision fatigue, when we're so exhausted that we give up-andjust pick something already.We're human. We can only process so much, and we can never be completely rational. Or can we?
For critical investments like cybersecurity, logic and structure must rule the day. There's always a new threat, a new breach, a new technology to buy. Fear, Uncertainty, and Doubt (FUD) is an acronym so well-known in the industry that, well, everyone knows it. It sells. The challenge is seeing beyond scare tactics and focusing on wise choices that matter.
Imagine if we could program a computer to make sound, objective cyber investment decisions. It would function like this:
The best part of this programmatic approach? Getting the most out of your cyber investments.
Simple advice is often hard to follow. Eat more vegetables. Exercise each day. Get 8 hours of sleep. Unless the Matrix is reality (who can say for sure), reality is nuanced and complicated. Our IT environments certainly qualify as complex, and so is organizational structure and the politics of decision-making.
The traditional approach has security as a cost center in its own silo. It spends money hoping to stay compliant and avoid a breach, often reacting to the latest headline. There's no way to measure success, business value, or the return on any cyber investments. And yet it somehow manages to get even more money when there's a compliance finding or security lapse. It sounds nothing like the programmatic approach we described, yet you'll find this is all too common.
On the other hand, the programmatic approach requires discipline, patience, and a wide base of support. It demands hard-to-find expertise and resilience despite near-constant organizational change. It's rational, and rational is boring. The bottom line is that it's the road less travelled becauseit's hard. Or is it?
Rational might be boring but, in cybersecurity, excitement often arrives in unwelcome forms. If you want to make big strides in cyber improvement, make the most of investments, and successfully mitigate risk, then take that less-traveled road. It's not has hard as you think.
Imagine if this was your reality:
You can start with a simple programmatic approach, like the one found in the NIST Cybersecurity Framework. It's less than 40 pages of programmatic, risk-based magic. Or ISO-27001. It outlines how to instill the mindset in your organization and improve your cyber approach with it.
But I won't just leave you hanging. Stay tuned for the next installment, where I'll describe how you can successfully transition to a programmatic approach to security in your organization.
Next steps: Learn more about
Cisco Solutions for Cybersecurity in Government
 Hot Tags :
Cybersecurity
National Cybersecurity Awareness Month (NCSAM)
#GovernmentNow
Hot Tags :
Cybersecurity
National Cybersecurity Awareness Month (NCSAM)
#GovernmentNow