


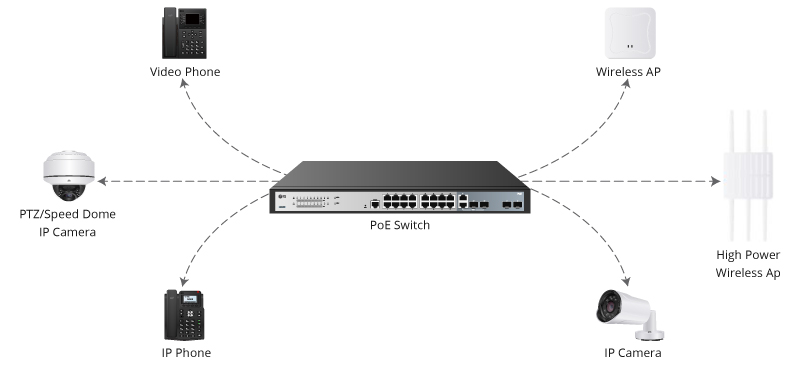

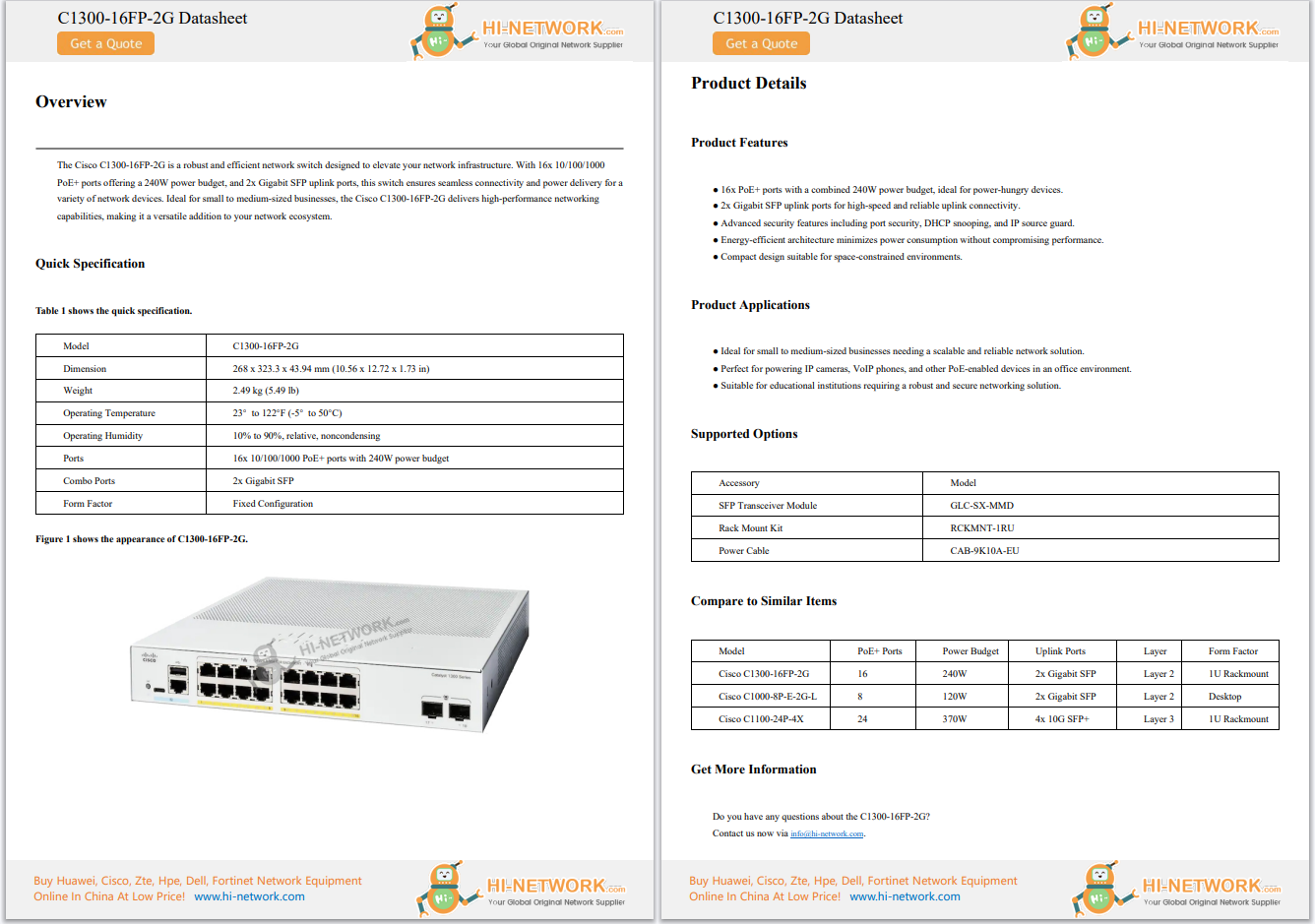






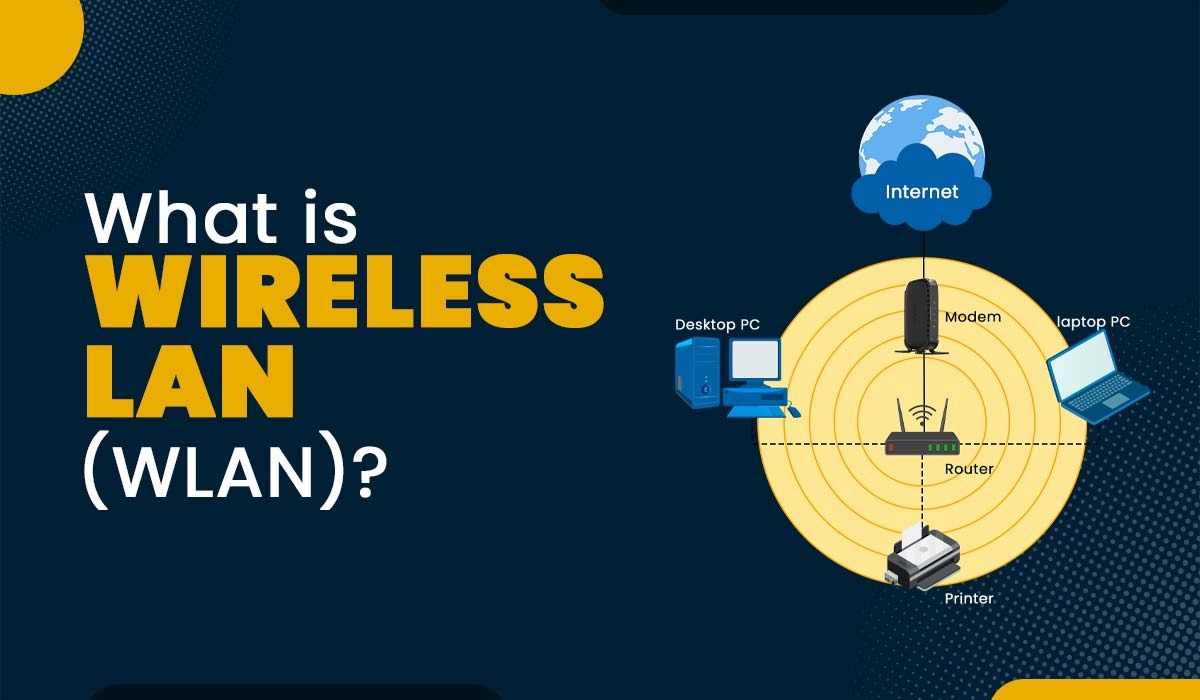






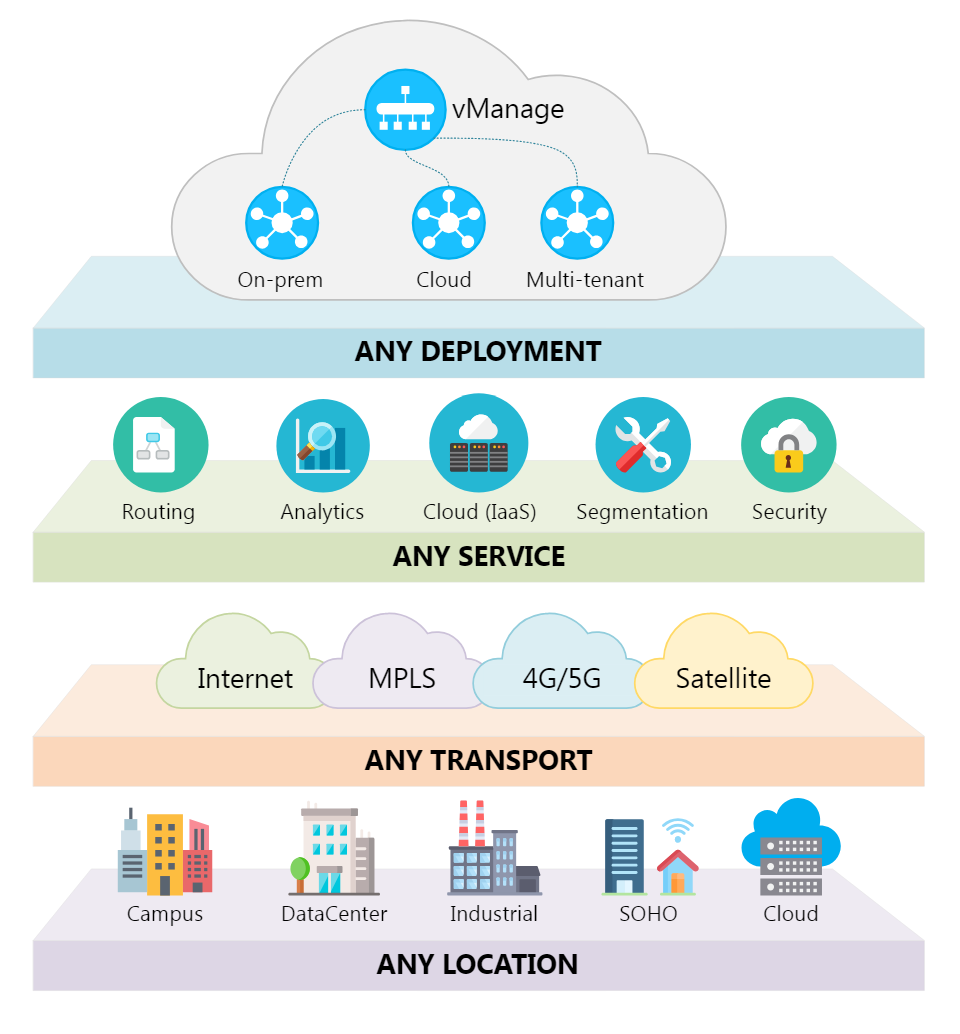
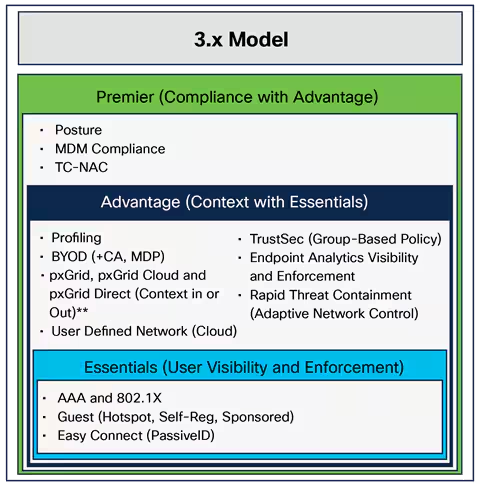

We live in the age of digitization. Digital tablets are replacing books, we get our news from RSS feeds instead of newspapers, "records" are being released as MP3s, and cars will soon be driving themselves. Yet at the same time, m...

By Ted Rose, Operational Security, Service Provider Video Software and Solutions, Cisco Our security team already blogged about the complex realities of securing digital video content back in April, when attendees of the National ...

The annual NBA Draft is all about finding the latest and greatest basketball talent; players who will someday become the face of franchises around the league. It's where their lifelong dreams of playing in the NBA become a reality...

The Internet of Things (IoT) is on course to transform businesses and create new revenue opportunities - is your organization ready to exploit it? It's a recurring topic of interest that crops up frequently during my conversations...

From the U.S. to the U.K. (and everywhere in between), Cisco is enabling schools and universities to#LearnWithoutLimits through the use of digital technology. As schools are put under constant pressure to compete for new students,...

Visibility has always been a core component of building effective security policy. Starting with the discovery phase of understanding the behavior of the users and assets on a network through the effective monitoring of the policy...

Life is what happens to you while you're busy making other plans.-John Lennon Giving back to the community is an important part of Cisco culture, and Cisco encourages volunteerism. They make it pretty easy, too, by planning volunt...

On Friday, billions of people will tune in to watch or listen to the start of the greatest sporting spectacle in the world. As a sports fan, I am excited to see the amazing performances to come, and already prepared with a box of ...

To prevent a security breach and loss of critical business data, security teams must be diligent in defining, identifying, and classifying security gaps in their organization's network. Many security teams conduct pentesting as a ...

We all know that there's a lot of hype around cloud computing. While many companies won't move their data to a public cloud anytime soon, the private cloud option is very compelling. IDC estimates thatspending on private...

Intelligence Gathering 101 Traffic analysis is rapidly becoming critical for threat analysis and incident response teams, and a choke point on their capability to be effective. Performing analysis on incoming threats requires secu...

I was recently asked how utilities are being disrupted by Digitization, distributed energy resources, and technologies such as the Tesla power wall, the Nest thermostat, etc. First is digitization, which is a broad term referring ...