



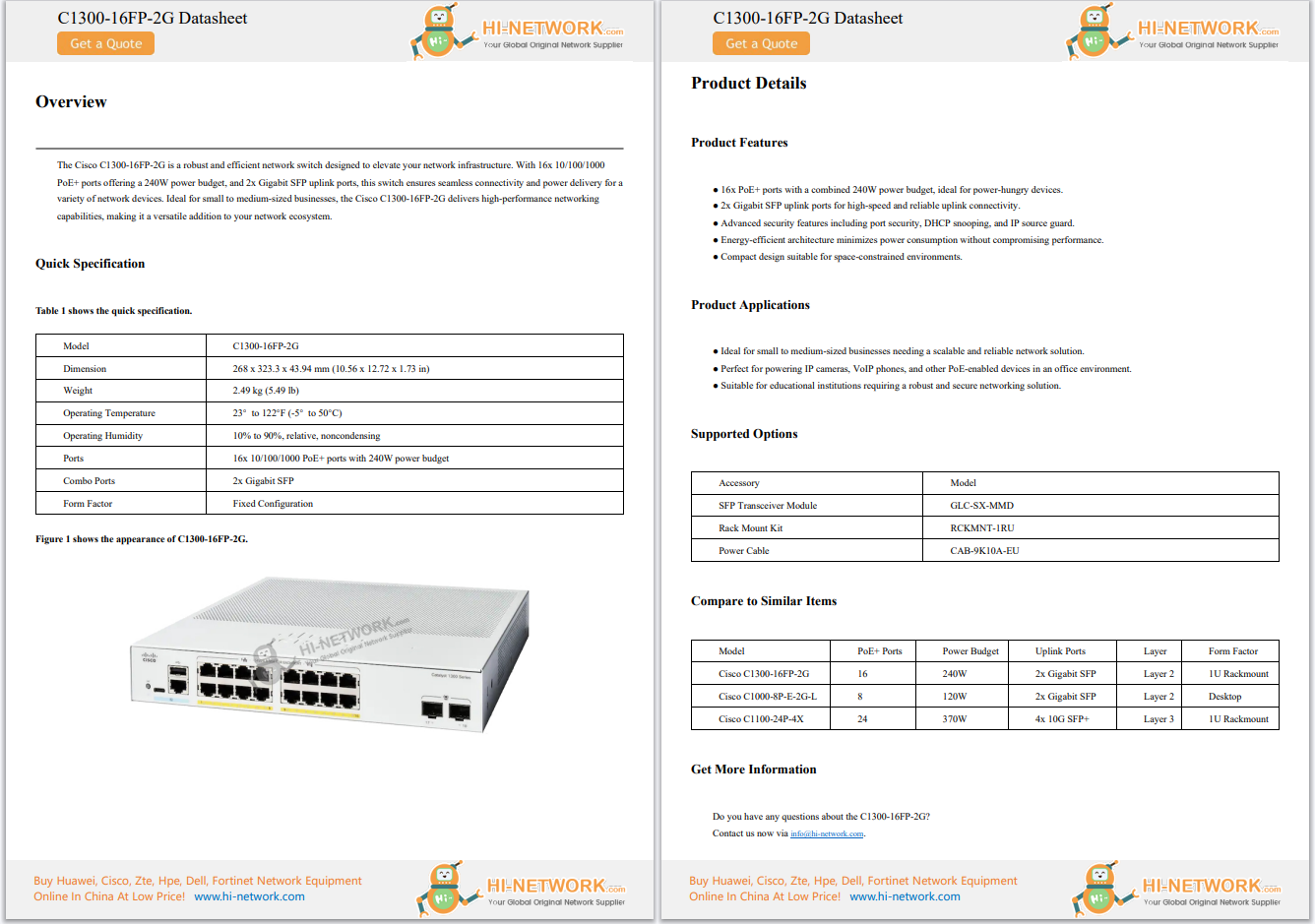
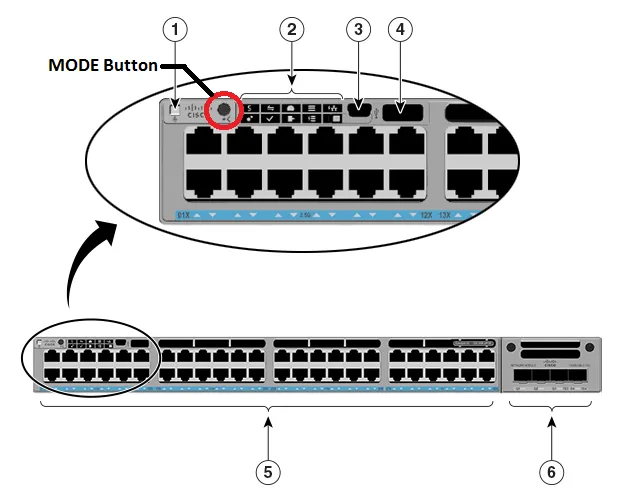




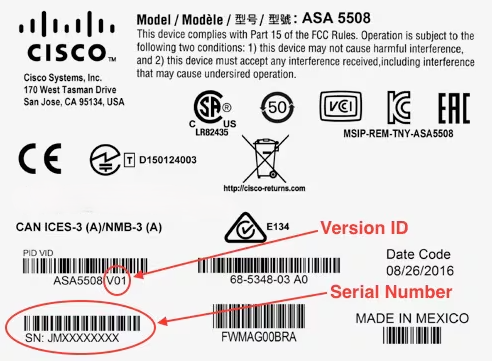








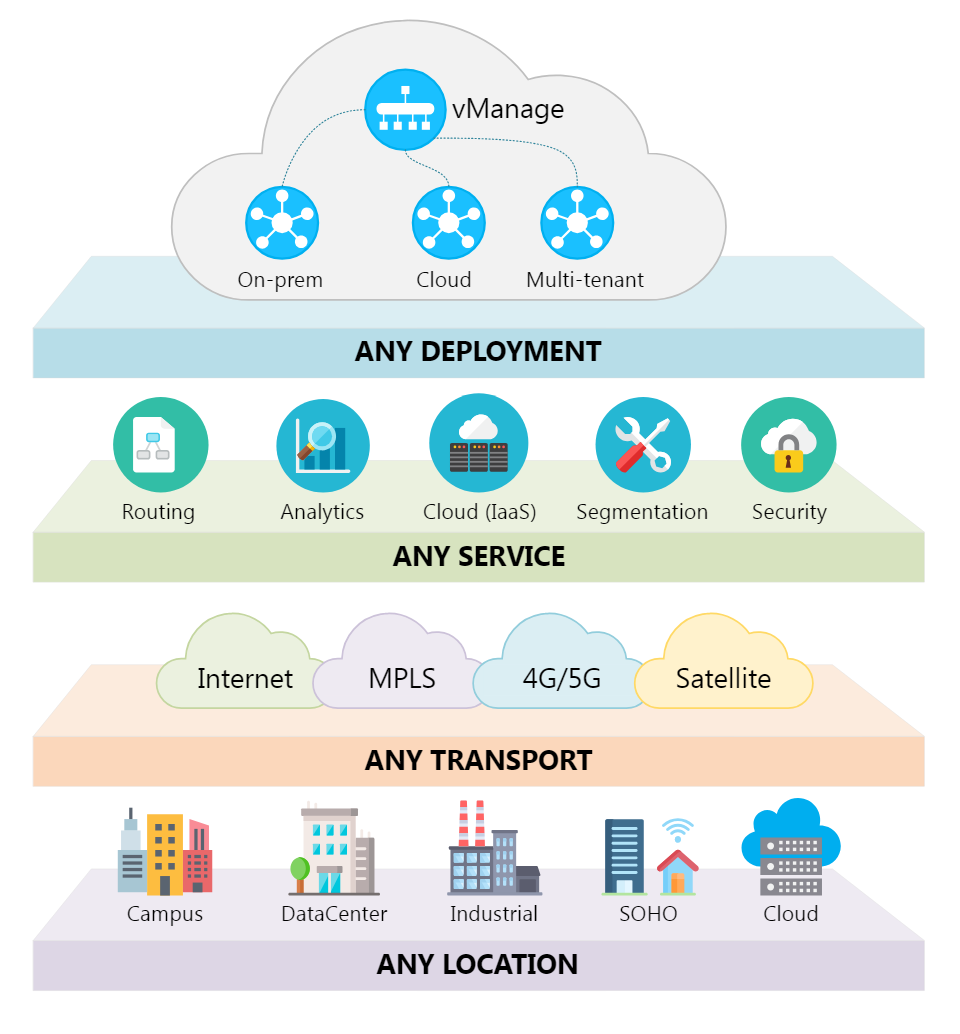
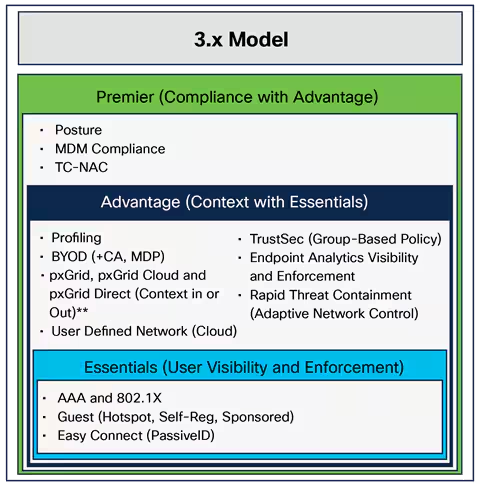

June is one of my favorite months of the year because the beginning of summer is also the time for our largest conference of the year -Cisco Live! This year, Cisco's annual conference of innovation was on full display in sunny Orl...

As marketers, we've come a long way in becoming data-driven experts when it comes to creating more engaging personalized marketing experiences. GDPR is making us think more critically about how we leverage data, maintain customers...

Energy and specifically electrically powered devices and appliances are part of everyday life for all of us. However, the dependency on personal computing devices like phones, tablets, headsets and the likes has made us realize ho...

As security practitioners, we have the seemingly impossible task of defending an ever-changing environment. It seems like every time we get close to compliance, new vulnerabilities and threat vectors are discovered. So, we continu...

Recently, I became a millionaire! Well,technicallyI'm a millionaire, even though my bank account may reflect otherwise. During a recent conference where I was talking about blockchain technology, I created a blockchain based crypt...

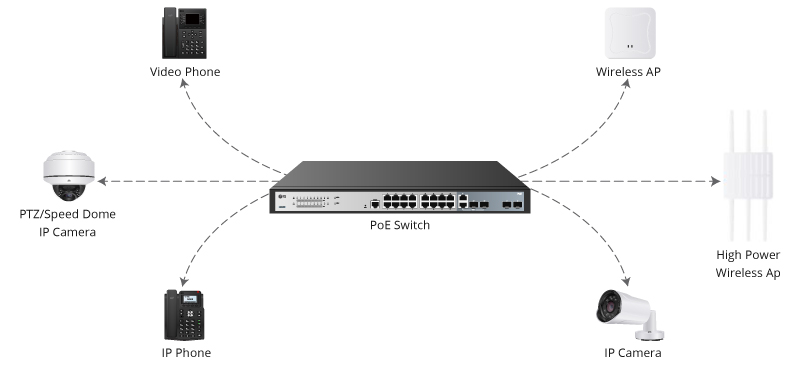
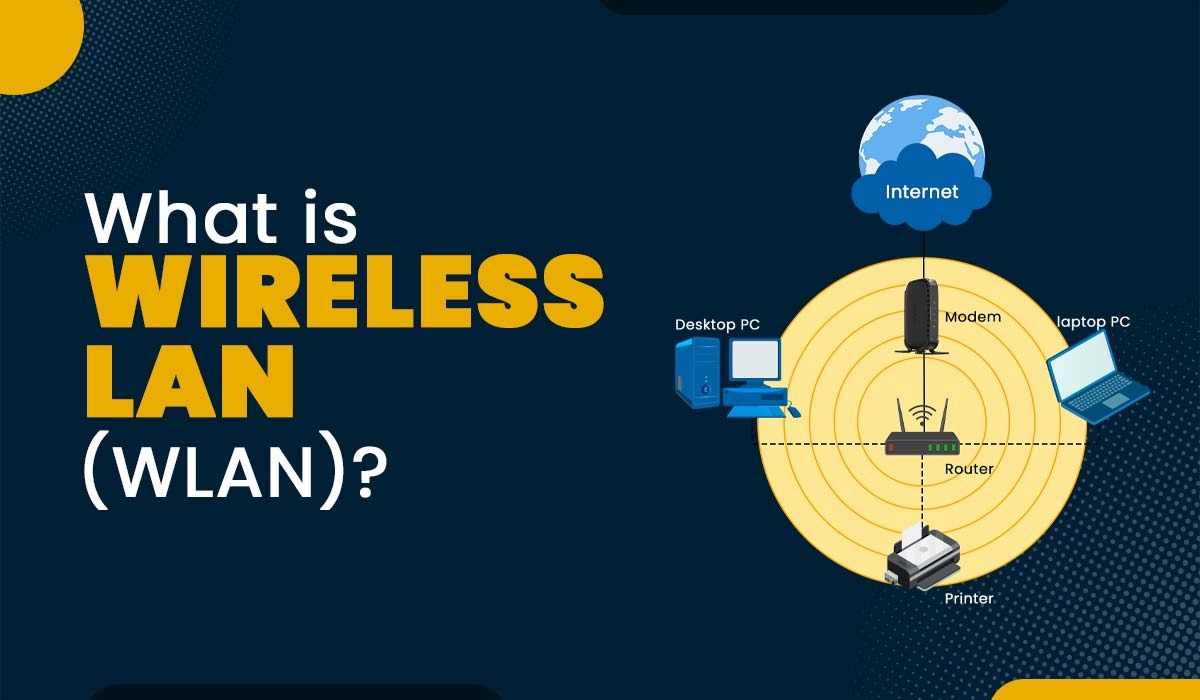
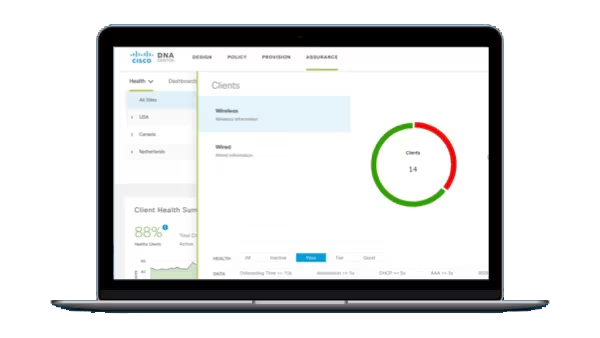
Background|I|have written a number of blogs on Network Plug and Play (PnP) on APIC-EM and wanted to provide an update of the new improved PnP in Cisco DNA Center. This new series covers the changes and enhancements made to Pn...

Today, as we do every week, Talos is giving you a glimpse into the most prevalent threats we've observed this week - covering the dates between June 29 and July 6. As with previous roundups, this post isn't meant to be an in-depth...

Recently, researchers have uncovered new attacks against the Long-Term Evolution (LTE) network protocol. LTE, a type of 4G network, is a mobile communications standard used by billions of devices around the world. Security researc...

Whether visiting a mom n' pop shop on Main Street or a luxury store on Fifth Avenue-customers will come in asking for relevant, personalized experiences. Customers expect retailers to engage them in a highly tailored and consisten...

This blog was guest-written by Jude Ower, founder, and CEO of Playmob. She'll be guest-speaking during the "Harnessing the Power of Technology for a Better World"sessionof theWomen Rock-ITseries on July 11. When you think of a typ...

For many service providers, the digital transformation journey may not be the smoothest. Many service providers (SP) are going through a phase where they are either trying to understand the new technologies or in the process of ea...

Time is critical when facing an incoming attack. Security analysts and incident responders must quickly detect, investigate, understand, and react quickly to limit any potential damage. They sift through threat intelligence inform...