















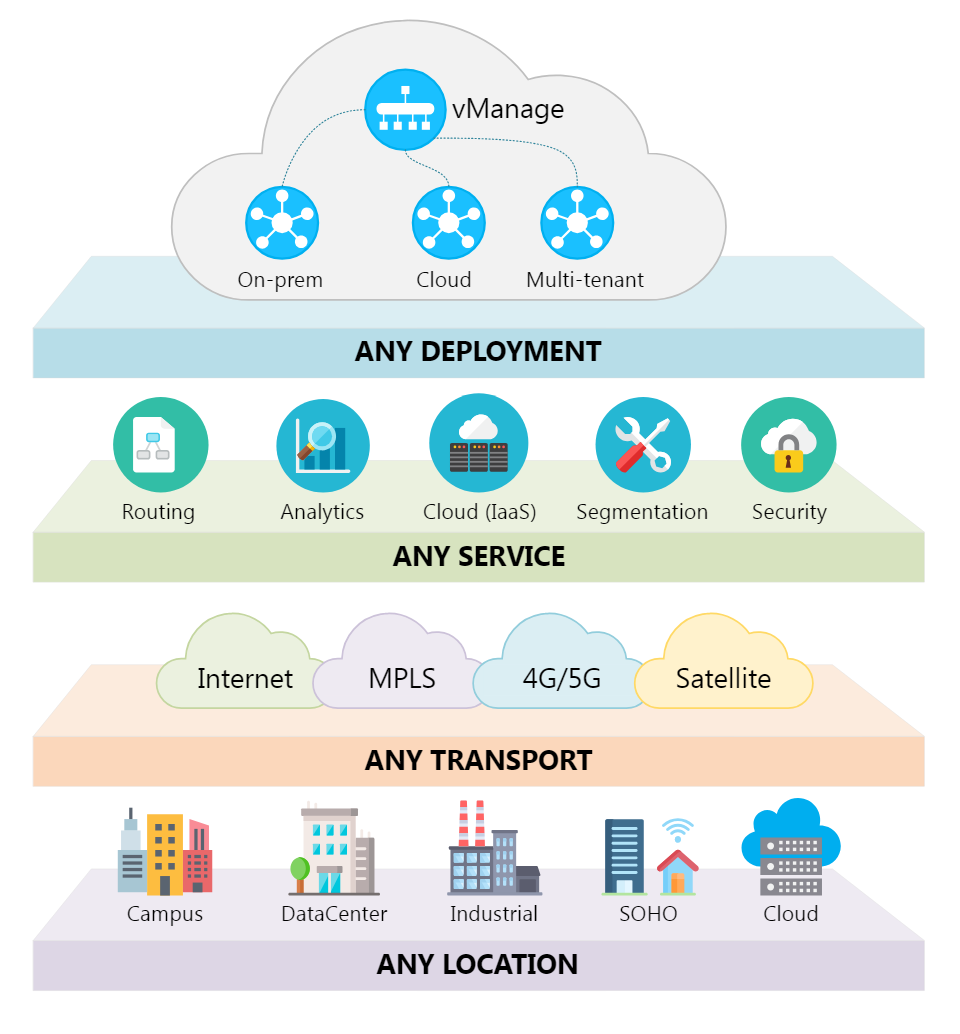
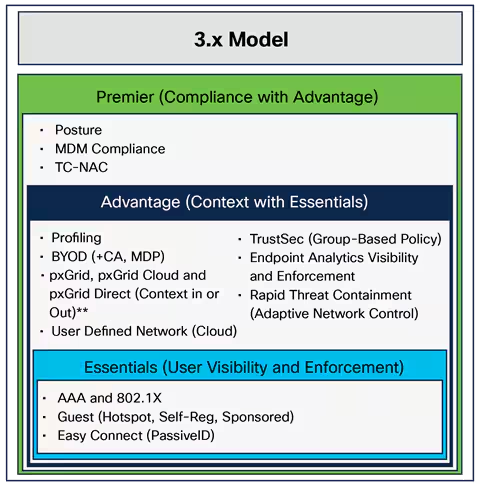

In this episode, our Cisco Champion host Denise Donohue discusses Stealthwatch with TK Keanini and Sandeep Agrawal. Get the Podcast Listen to this episode in SoundCloud SUBSCRIBE on iTunes and listen to all episodes of Season ...

The last time I was in a hospital was to visit my friend. Her mom was sick, and I went to keep my friend company. We decided to meet in the cafeteria. The Lyft dropped me off at the ER, and then I wandered through the massive hosp...

This blog post was authored by Edmund Brumaghin and Holger Unterbrink with contributions from Eric Kuhla and Lilia Gonzalez Medina. Overview Cisco Talos has recently observed multiple campaigns using the Remcos remote access ...

Have you realized that companies' transformation towards Digitization ironically drive easier consumption models while technology behind it gets often more complicated? When I get a chance to sit on a table to discuss Digitization...

As more and more organizations move from self-hosted infrastructure to cloud-based environments, so too increases the demand to ensure that they are resilient and secure. As part of Cisco's efforts to support our customers in maki...

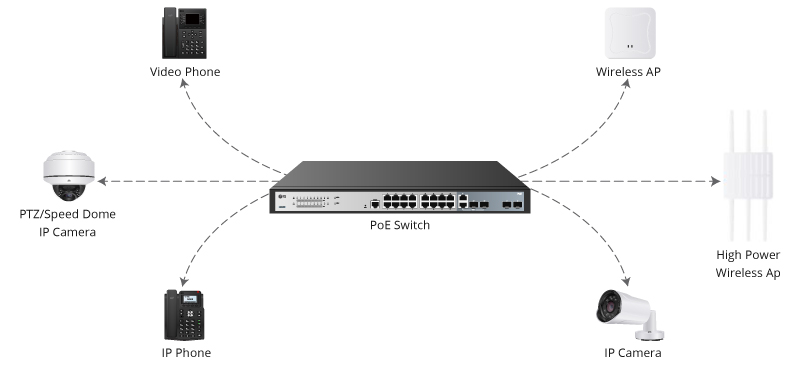
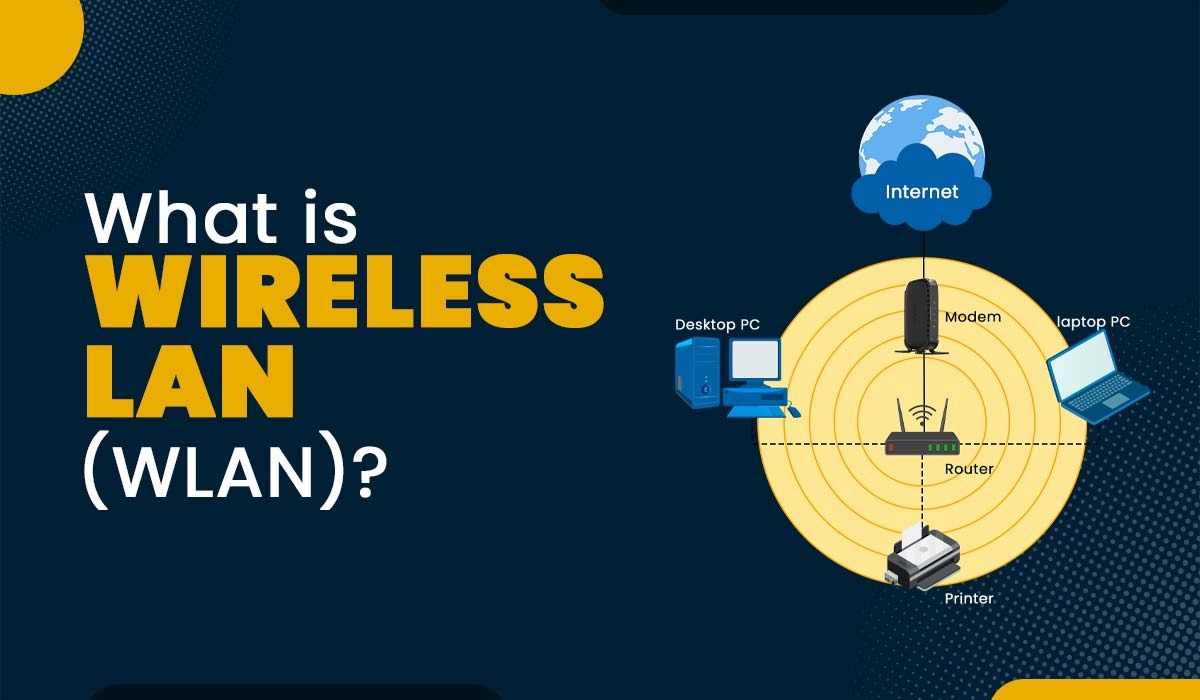
Technology innovation is advancing faster than ever before in history. With this rapid growth, the number of devices and network connections can become overwhelming to manage. To bring to life just how staggering this growth...

Prior to joining Cisco, I lived the start-up life for many years. What drew me to the start-up culture was the fact you can build and create new things all the time and work on different, exciting projects -my fear of losing...

Watch below to learn how to use the most popular features in Cisco Tetration. Bookmark this page because new videos will be added. Demo: Introduction to Cisco Tetration User Interface (UI) Demo: How...

What doesn't kill us makes us stronger. We resist gravity, and our muscles become stronger. We negotiate conflicts, and our emotional intelligence increases. But what if this also applied to IT systems? The next generation of netw...

We are a long way away from the day when all of InfoSec can run autonomously using machine learning (ML). We, humans, are still the most advanced component in the InfoSec chain, and we will be for some time. We have the experience...

In the past few years, we have seen a surge of advancement in cloud development. New platforms, developer tools, and cloud services have become available, and developers have responded by building innovative cloud-based applicatio...

Preventing malware incidents is very much like preventing bad things from happening in our day-to-day life. We all take precautions every day (well, most of us do, anyway). Actions as simple as carrying an umbrella when rain is fo...