



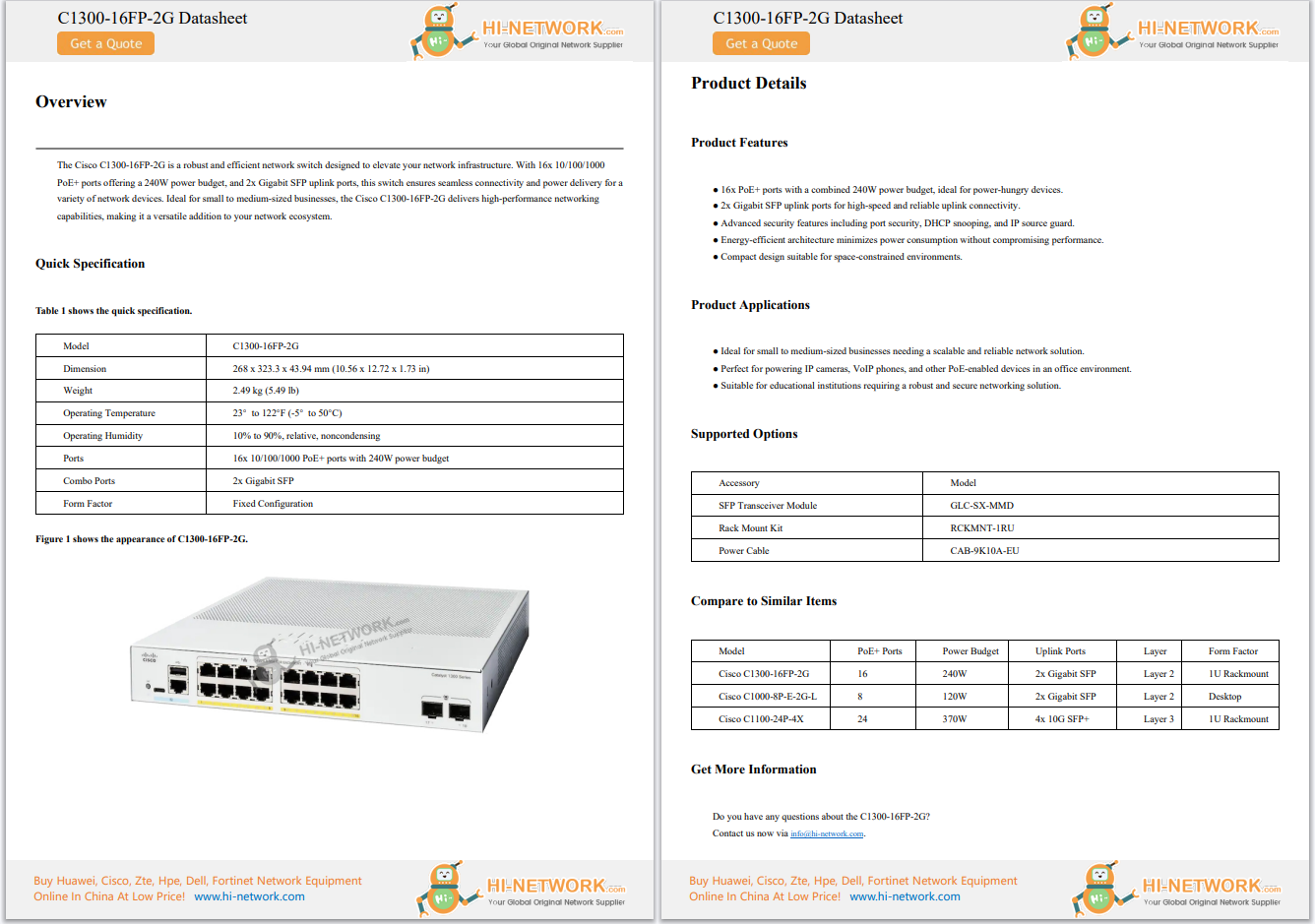
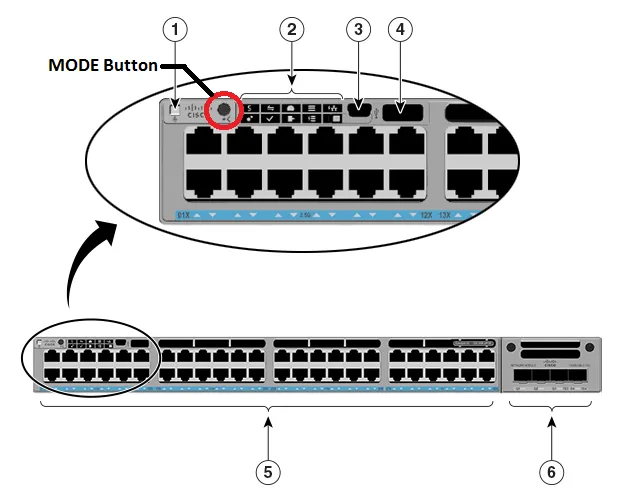




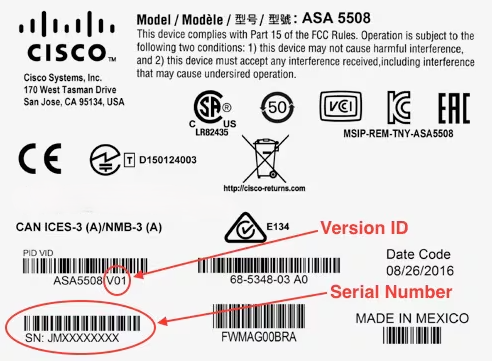








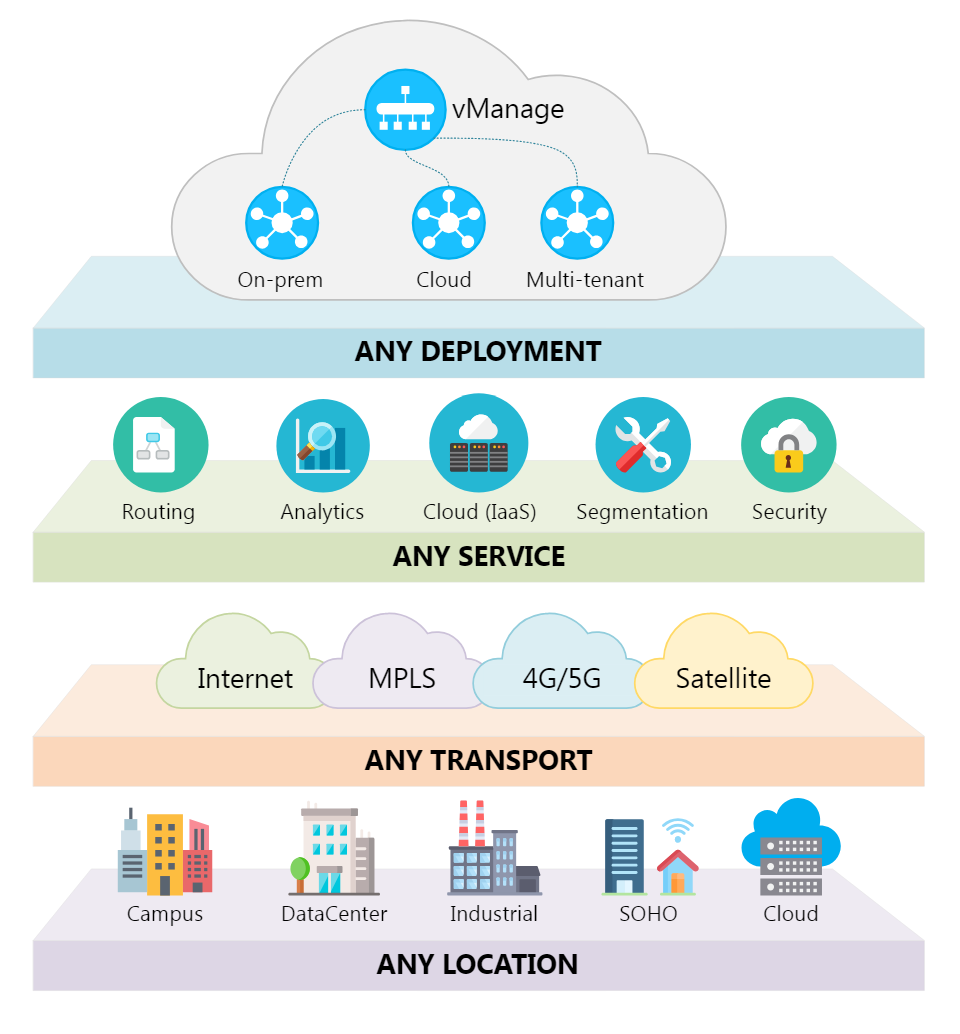
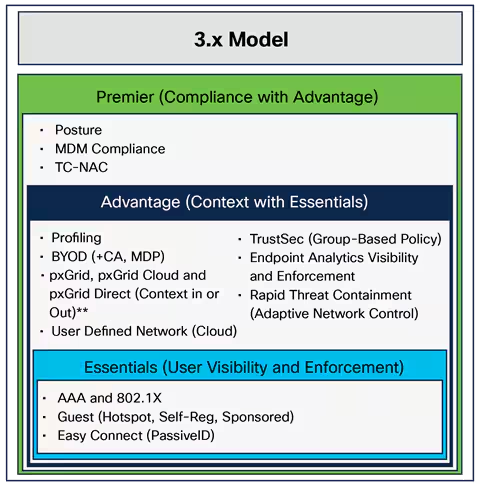

As the daughter of an excellent railway engineer, I had never imagined myself to be an engineer. But then, during my last semester of graduate school, my plan changed when I learned about a company called Cisco. Prior to this mome...

Last week, my colleagues Tim Fawcett, Matt Carling and I had the honor and pleasure of representing Cisco in a hearing before the Australian Parliamentary Joint Committee on Intelligence and Security. The topic: pending legislatio...

I|like|Cisco Chats because they give us an opportunity to connect with our global Developer Community. It's a time for Cisco programmability experts to share helpful information that can guide you in your new or ongoing projects. ...

Last year, Cisco announced its vision to extend ACI into the public cloud domain and introduce key attributes -unified security policy, single-pane-of-glass management, and visibility -for Amazon Web Services (AWS), Google Cl...

How|encoding|and transport of the data-model gives you power and flexibility In the first blog, I attempted to make the point that the declarative approach of using function-specific modulesinAnsible is not scalable. In the second...

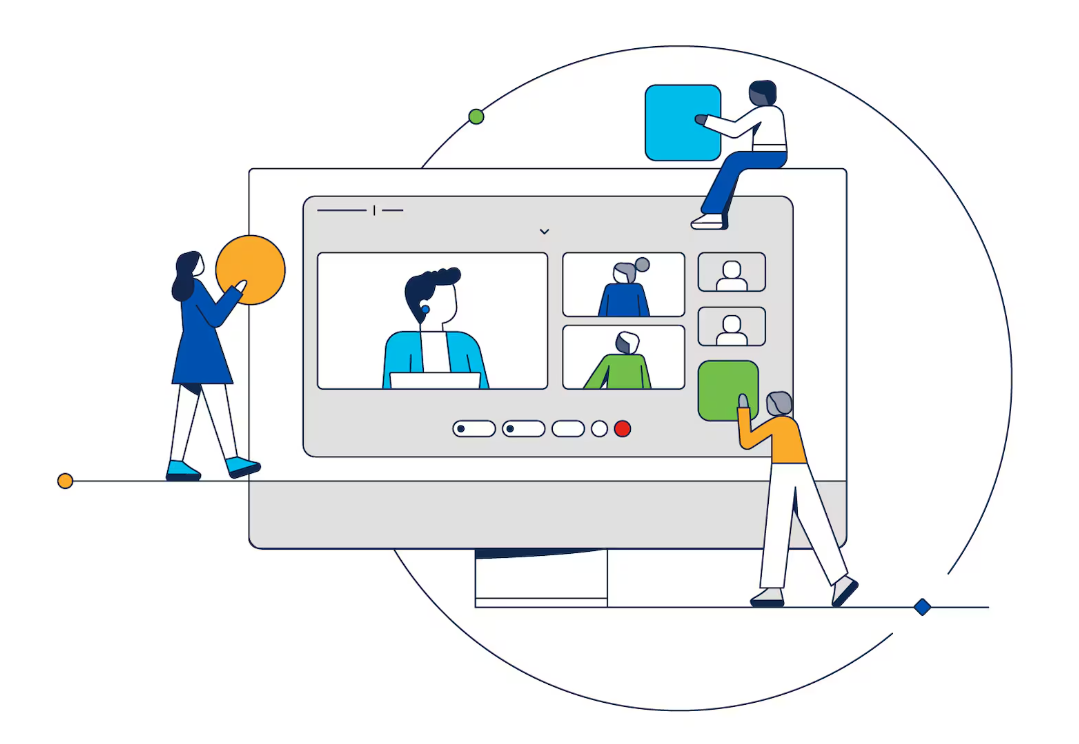
I know firsthand that Cisco Webex Meetings has made the online meeting experience easier than ever. Each month, 130 million people rely on Webex to collaborate better and work faster. With Webex Meetings, they now enjoy video conf...

This is an exciting day for healthcare IT leaders who've been working to integrate information technology into care delivery. Today, HIMSS Analytics announced its new Infrastructure Adoption Model or INFRAM. The INFRAM measures th...

It took over 20 years for the automobile to begin showing its dominance in transportation with the best-selling Model T. Even when the Model T saw its production end in 1927, the infrastructure and ecosystem for the car were still...

Nowadays when people think of Oil & Gas they tend to link this industry with pollution, depletion of natural resources and super-rich countries that base their economies and lifestyle on the extraction of these fossil fuels in...

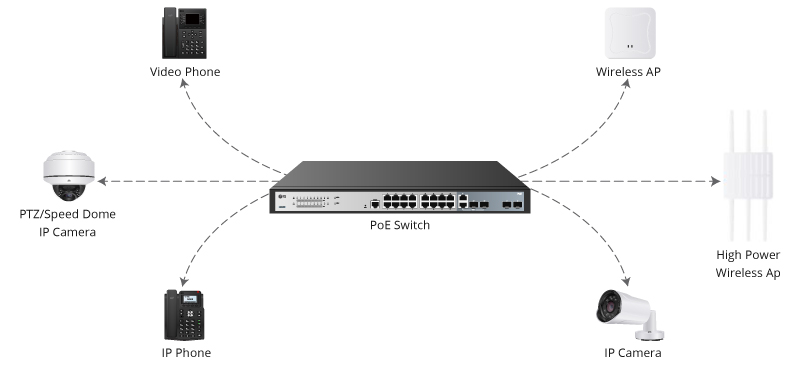
It is no secret that the proliferation of connected devices and sensors has introduced new and growing security challenges across every industry and enterprise. The question is no longer whether or not a device or sensor is digita...

There's no silver bullet for online security, especially when it comes to user authentication. And enterprises aren't alone in the struggle to keep up with the needs and demands of authentication. At the center of all of this lies...

As George Box noted several decades ago, "All Models are essentially wrong, but some are useful". The work of statistical analysis, and its modern day derivatives of Machine Learning and Deep Learning, continue to be bold at...