


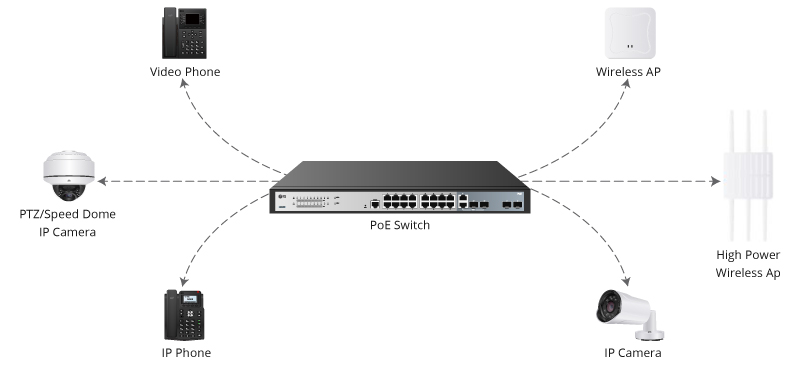

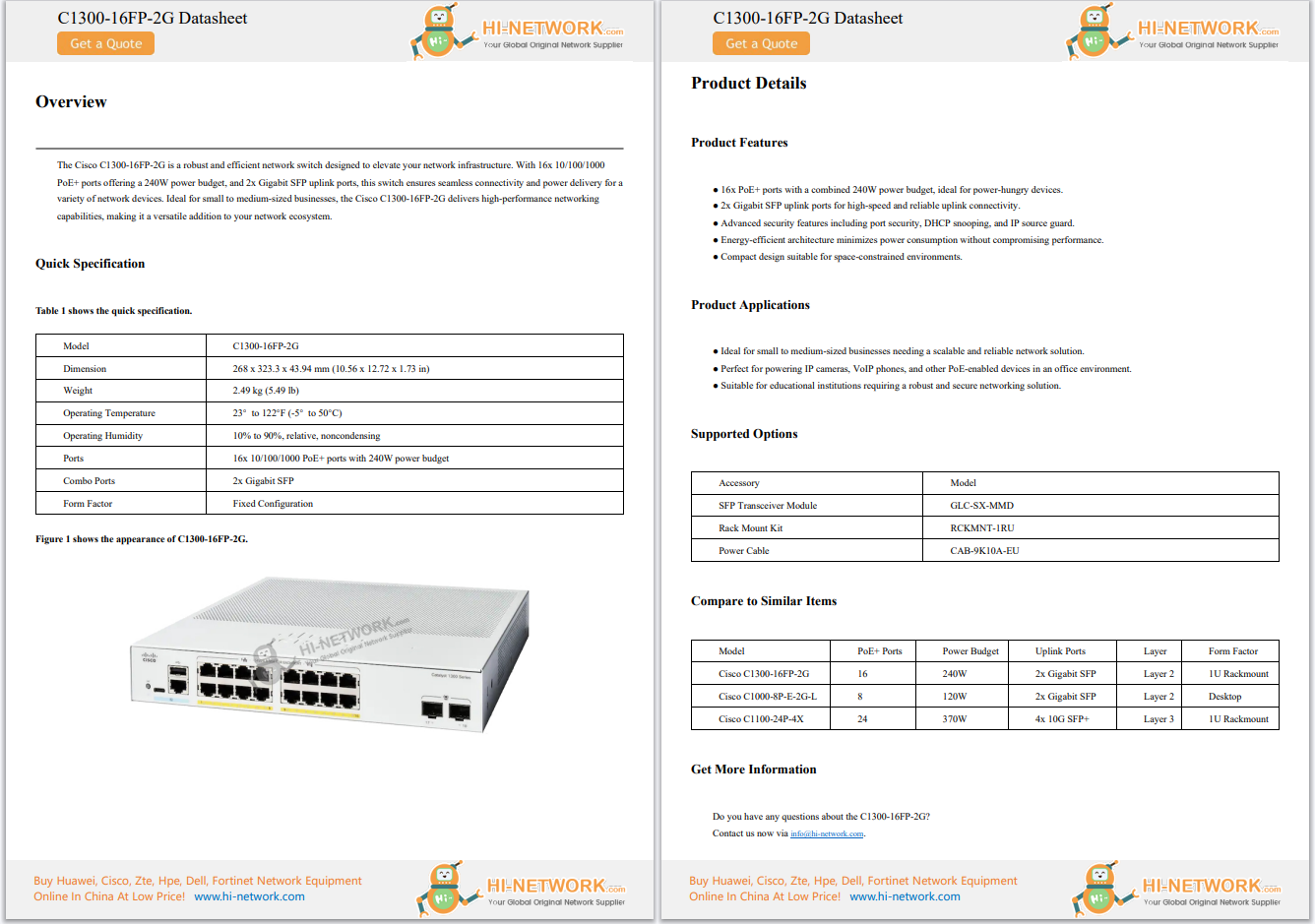
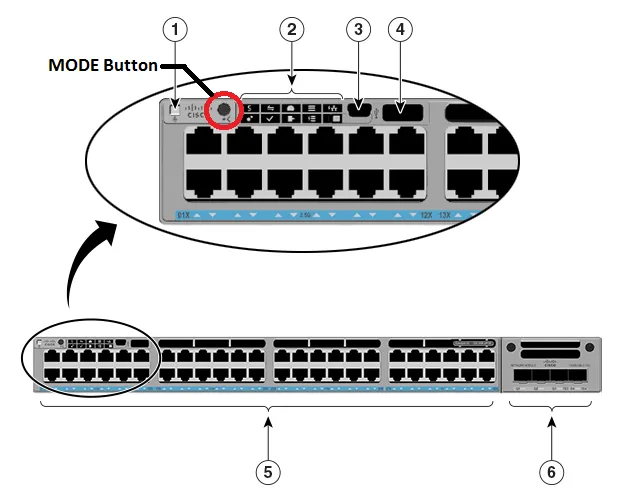




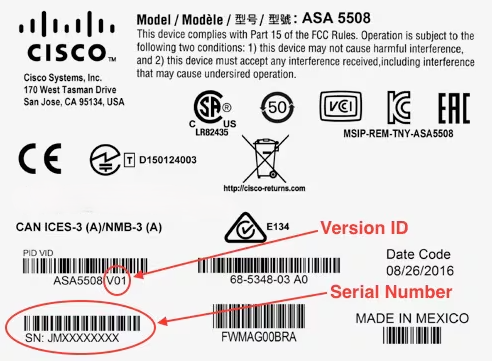


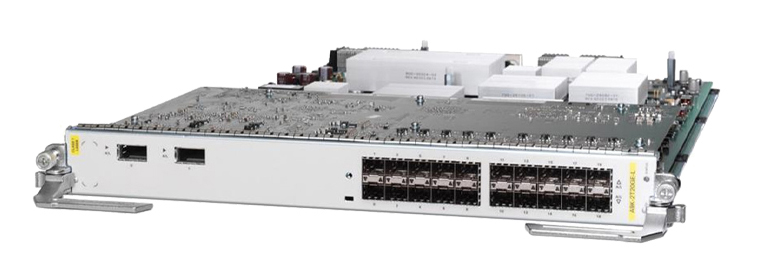







When new hardware is ordered and it arrives on site, it

Edmund Brumaghin and Holger Unterbrink authored this blog post. Executive summary Malware designed to steal sensitive information has been a threat to organizations around the world for a long time. The emergence of the greyware m...

In a previous blog onCisco Trusted PlatformsI looked at the hardware Trust Anchor module (TAm) that enhances the security of Cisco Service Provider products and provides visibility into the authenticity and integrity of the platfo...

Cisco Talos is disclosing a series of vulnerabilities found in the Shimo VPN Helper Tool. Shimo VPN is a popular VPN client for MacOS that can be used to connect multiple VPN accounts to one application. These specific vulnerabili...

The Philippines is one of Asia

Black Hat 2019 returned to Singapore with Black Hat Asia with four days of Trainings and Briefings, with the Business Hall. Cisco Security is proud to be a Technology Partner of Black Hat in the Network Operations Center

Today, Talos is publishing a glimpse into the most prevalent threats we

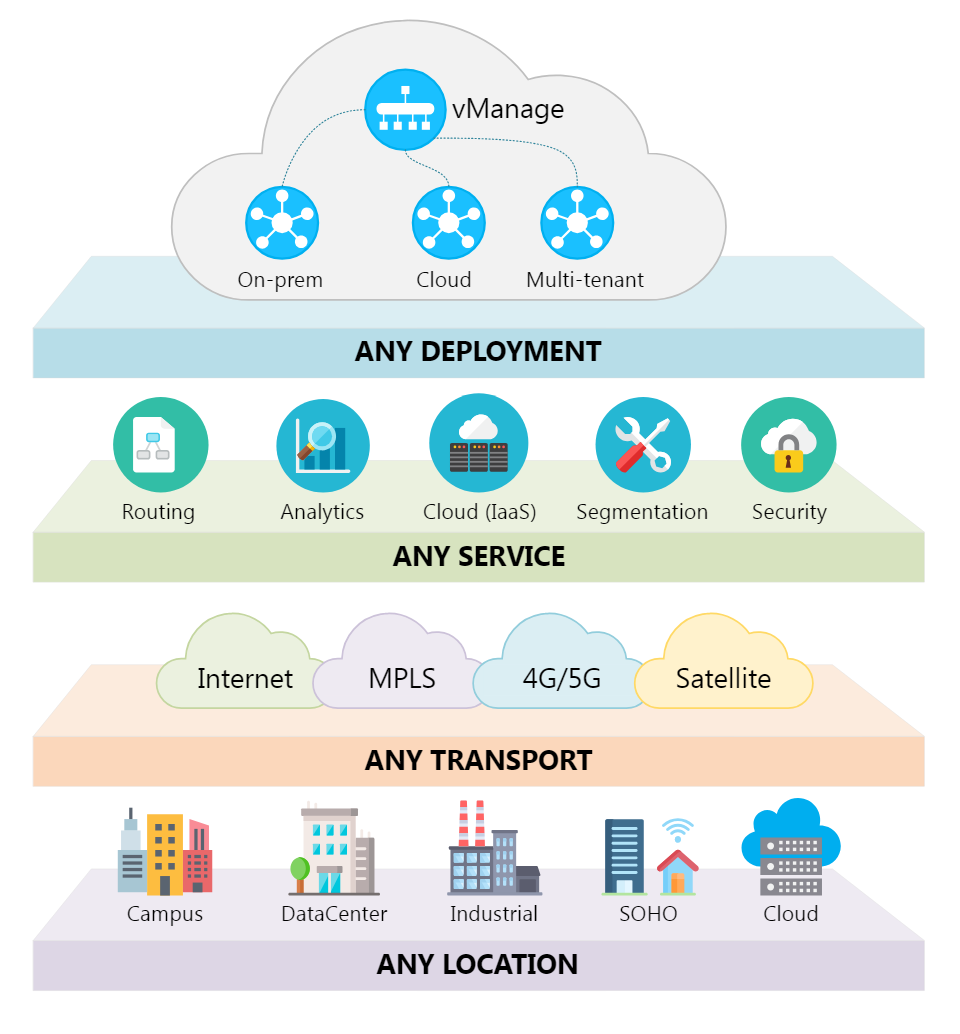
In this episode of Cisco Champion Radio, we chat with Adrian Iliesiu about developing with SD-WAN and how you can streamline your workflow with vManage. Interviewing Adrian are Cisco Champion hosts, Daren Fulwell and David Pe...

Partner Success Story In the pursuit of knowledge, creativity knows no bounds. Or so they say. But administrators at the Parkland School District in northern Alberta, Canada knew its teachers and students were missing out. Schools...

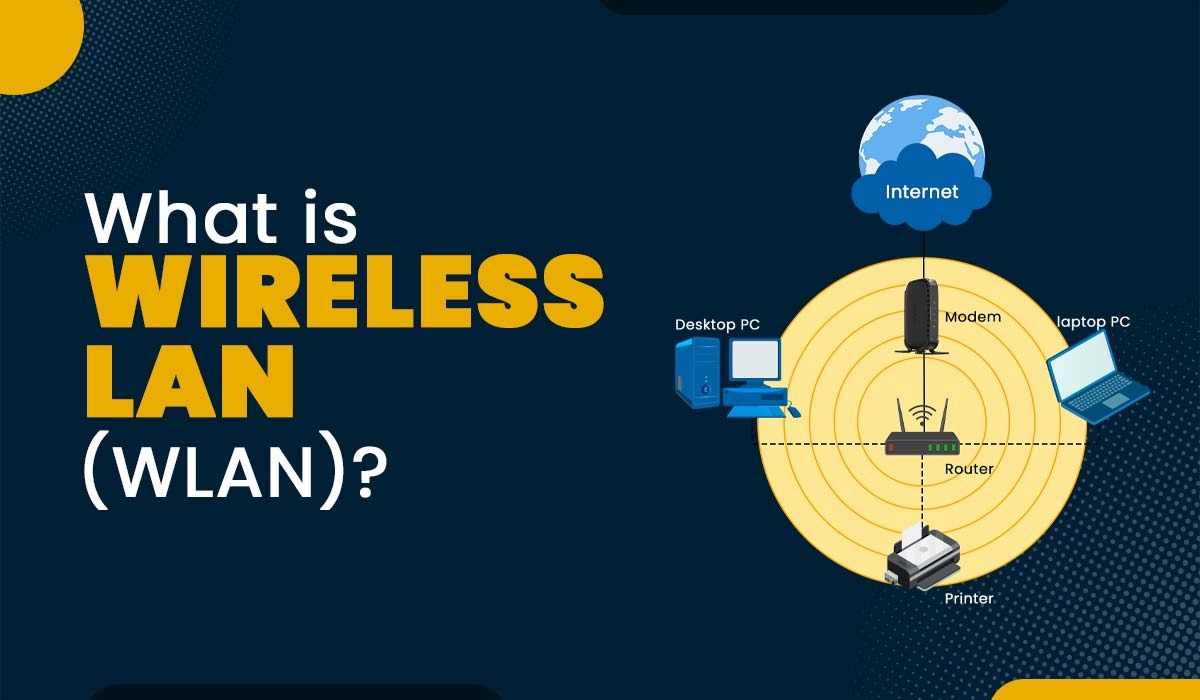
Simplifying the IT architecture is super important for retailers

Post authored by Nick Biasini and Jaeson Schultz. Sextortion spammers continue blasting away at high volume. The success they experienced with several high-profile campaigns last year has led these attackers to continue transmitti...

Cisco is working continually to bridge the nation