












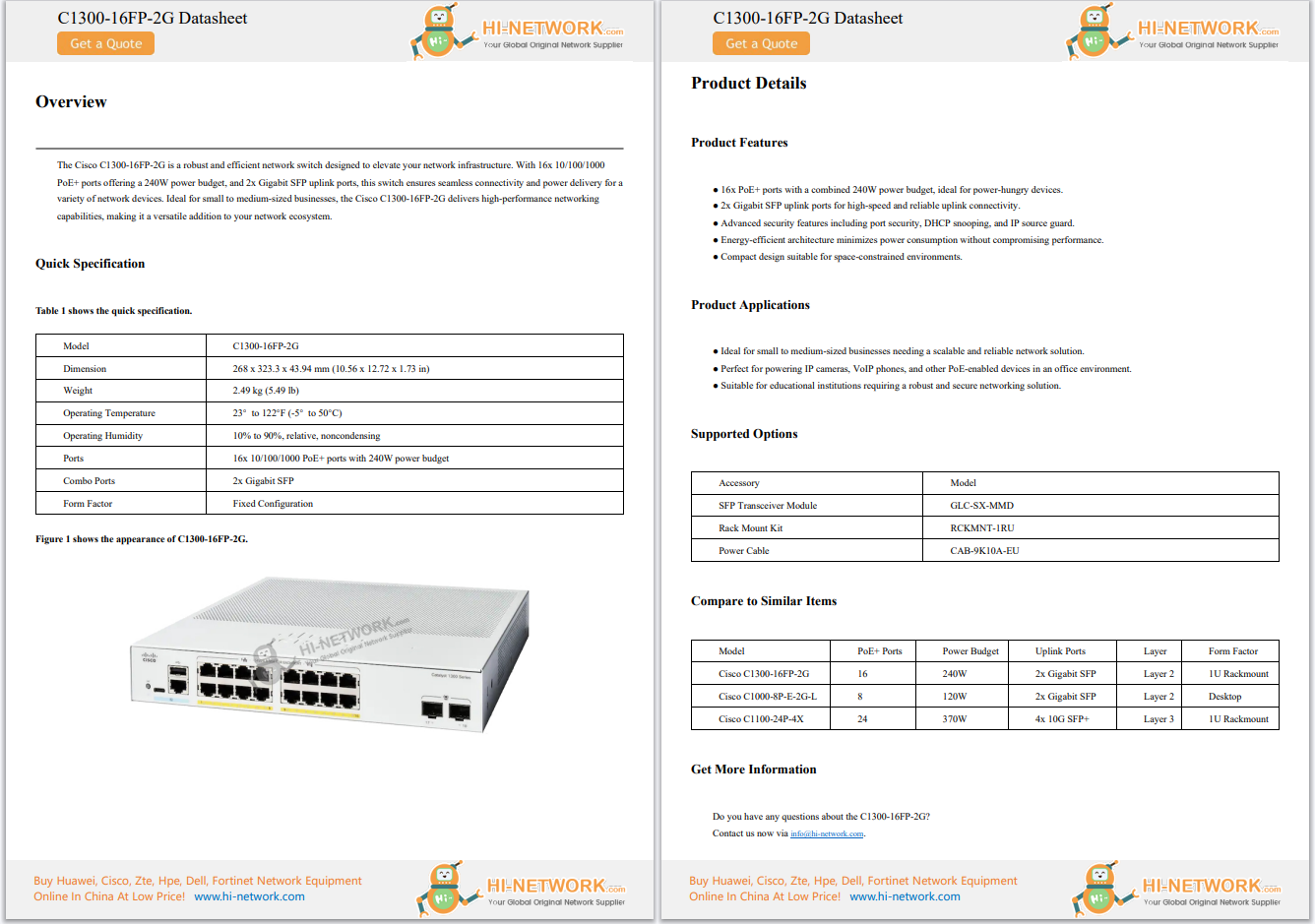






This is the second in our series of blogs about the quantum threat and preparing for "Q-Day," the moment when cryptanalytically relevant quantum computing (CRQC) will be able to break all public-key cryptography systems in operation today. The first blog provided an overview of cryptography in a post-quantum world, and this one explores what comes next.
The US government directed the National Institute of Standards (NIST) to develop new quantum-resistant cryptographic standards out of concern about Q-Day and "harvest now, decrypt later" (HNDL) risks. NIST has now released the final standards for the initial PQC algorithms. This is an impressive and rare consensus among industry stakeholders and the research community holds that the standards' algorithms represent an effective means to mitigate quantum risk. However, the standards alone are not enough to realize the goal of quantum-safe computing in practical terms. The standards are key to developing PQC solutions, but they are not a fait accompli. Operationalizing them will require more work.
To accommodate the new algorithms, it will be necessary to create new, or modify existing, transport protocols. These changes can range from simply allowing the selection of the new PQC algorithms, to developing completely new standards to address factors like larger key sizes and protocol limitations. The Internet Engineering Task Force (IETF) has been working on these issues and should be soon releasing the key standards for TLS, SSH, IKEv2, and others.
Crypto software libraries that support NIST's PQC algorithms and these protocol standards are being created and validated. There are a lot of moving parts, so the process promises to be challenging. Industry groups like the Linux Foundation's Open Quantum Safe (OQS) project have the potential to smooth the transition by facilitating agreement on standards implementation. OQS is part of the Linux Foundation's Post-Quantum Cryptography Alliance, of which Cisco is a founding member. The project is focused on the development of liboqs, an open-source C library for quantum-resistant cryptographic algorithms, as well as on prototype integrations into protocols and applications. This includes a fork of the OpenSSL library.
The IETF is also bringing industry stakeholders together to develop a new quantum-safe version of the Internet X.509 Public Key Infrastructure (PKI). This will incorporate algorithm Identifiers for the Module-Lattice-Based Digital Signature Standard (ML-DSA) that bring the public key infrastructure up to production quality.
Products will need to be updated to include these new crypto libraries and PKI capabilities. We expect products to provide PQC transport protocols initially, to address the harvest-now, decrypt-later (HNDL) vulnerability. The PQC PKI standards and industry support will likely take a bit longer to become available. As these are not directly involved in HNDL attacks, this delay does not currently pose a significant risk.
Cryptography is essential for secure functioning of computers and networking hardware. Cryptography makes it possible for hardware to establish trust with other hardware, as well as within itself, e.g., the operating system (OS) trusting that the hardware has not been compromised. Making hardware quantum safe will therefore mean updating a variety of hardware components and functions that rely on cryptography.
For example, the Unified Extensible Firmware Interface (UEFI) needs to be adapted so it can handle PQC algorithms and keys. Similarly, chipmakers will have to revise Trusted Platform Module (TPM) chips to support PQC standards. This affects servers, network hardware, and storage. As quantum-safe UEFI and TPM become available, hardware makers will then have to redesign products that depend on them for security. This is a two-stage process-chips first, products later-that will affect the timeline for delivering new quantum-safe hardware.
Cisco has offered quantum-safe hardware since 2013. Many products, including the Cisco 8100 router, Cisco Catalyst 9500 network switch, and Cisco Firewall 4515, provide quantum-safe secure boot using LDWM hash-based signatures (HBS), a precursor to the NIST approved LMS. Cisco's Secure Boot checks for signed images to help ensure that the code running on Cisco hardware has not been modified by a malicious actor. New quantum-safe editions of Secure Boot and Cisco Trust Anchor Technologies will be coming out soon, implementing the new NIST PQC standards. The Cisco white paper, "Post Quantum Trust Anchors," goes into depth about how Cisco establishes quantum-safe computing using HBS and PQ signatures.
Cisco PQC hardware based on the new NIST standards is expected to become available in late 2025 or 2026. The availability of Cisco products that utilize standard industry components, such as CPUs or TPMs, will be dependent on their availability. This will likely delay their availability until late 2026 or 2027.
What should you do to make sure you're ready for the next steps in the PQC journey? Visit the Cisco Trust Center to learn more about what Cisco is doing, the company's current capabilities and its plans for new PQC products and technologies. The next blog in this series will discuss the impacts of government regulations on PQC product availability.
 Hot Tags :
quantum-safe computing
post-quantum cryptography
Hot Tags :
quantum-safe computing
post-quantum cryptography